Z Trek: The Alan Zeichick Weblog

Being scammed in French – mais non!
This just in, via Facebook Messenger, from an account called “Clemond Fernand.” It’s a scam. Don’t reply to messages like this – block the account instead.
Bonjour,
Je réponds a tous ceux qui sont dans la mélasse comme moi niveau…

Oklahoma is not okay for spam scammers
It’s like this scammer isn’t even trying. Dr. George is disappointed in me for setting up and missing an appointment. Fortunately he went to bat and convinced someone to pay some fees to save my $5.5 million ATM card. If I reply soon and…

The magnificent lunar eclipse of January 31, 2018
We had a good show this morning! Enjoy these photographs, taken with a Canon EOS 1D Mk IV with a 500mm prime lens. The first image was cropped, and the last one had its exposure boosted in post-processing by 4 stops. Otherwise, these are untouched.
…

How to build trust into a connected car
Nobody wants bad guys to be able to hack connected cars. Equally importantly, they shouldn't be able to hack any part of the multi-step communications path that lead from the connected car to the Internet to cloud services – and back again.…

Five tech predictions for 2018
We all have heard the usual bold predictions for technology in 2018: Lots of cloud computing, self-driving cars, digital cryptocurrencies, 200-inch flat-screen televisions, and versions of Amazon’s Alexa smart speaker everywhere on the planet.…

Dell’s predictions for 2018: open networking digital transformation, merchant silicon
Tom Burns, VP and General Manager of Dell EMC Networking, doesn’t want 2018 to be like 2017. Frankly, none of us in tech want to hit the “repeat” button either. And we won’t, not with increased adoption of blockchain, machine learning/deep…

More than a billion exposed and breached data records
From January 1, 2005 through December 27, 2017, the Identity Theft Resource Center (ITRC) reported 8,190 breaches, with 1,057,771,011 records exposed. That’s more than a billion records. Billion with a B. That's not a problem. That's an epidemic.
That…

I don’t think this is a real job offer via LinkedIn
Hello, Terry, whatever your email address is. I don't think you really have a job offer for me. For one thing, if you really connected via LinkedIn, you'd have messaged me through the service. For another, email addresses often match names.…

The ketchup bottle meets cloud computing
The pattern of cloud adoption moves something like the ketchup bottle effect: You tip the bottle and nothing comes out, so you shake the bottle and suddenly you have ketchup all over your plate.
That’s a great visual from Frank Munz, software…

The benefits of being a lazy Java programmer
“The functional style of programming is very charming,” insists Venkat Subramaniam. “The code begins to read like the problem statement. We can relate to what the code is doing and we can quickly understand it.” Not only that, Subramaniam…

Alan in Swedish
At least, I think it's Swedish! Just stumbled across this. I hope they bought the foreign rights to one of my articles...

IBNS and ASN: Intent-Based Networking Systems and Application-Specific Networking
With lots of inexpensive, abundant computation resources available, nearly anything becomes possible. For example, you can process a lot of network data to identify patterns, identify intelligence, and product insight that can be used to automate…
All the Russian girls love me!
So many women in Russia are vying for my attention… and all of them, from Alina to Veronika, are using the exact same language. Needless to say, this is a scam.
The scammers try too hard. One message might have gotten someone’s attention…

Artificial Intelligence is everywhere!
When the little wireless speaker in your kitchen acts on your request to add chocolate milk to your shopping list, there’s artificial intelligence (AI) working in the cloud, to understand your speech, determine what you want to do, and carry…

Nothing says fake success like a pay-to-play fake executive award
“Proudly not pay-to-play, we invite all of this years’ recipients to share their success through a complementary digital certificate and copyright to the title.” So claims the award letter.
We received this email to our corporate info@…
Artificial Intelligence and Machine Learning are the future of software development
Millions of developers are using Artificial Intelligence (AI) or Machine Learning (ML) in their projects, says Evans Data Corp. Evans’ latest Global Development and Demographics Study, released in January 2018, says that 29% of developers…
Let’s applaud the new Wi-Fi security standard, WPA3
Wireless Ethernet connections aren’t necessarily secure. The authentication methods used to permit access between a device and a wireless router aren’t very strong. The encryption methods used to handle that authentication, and then the…
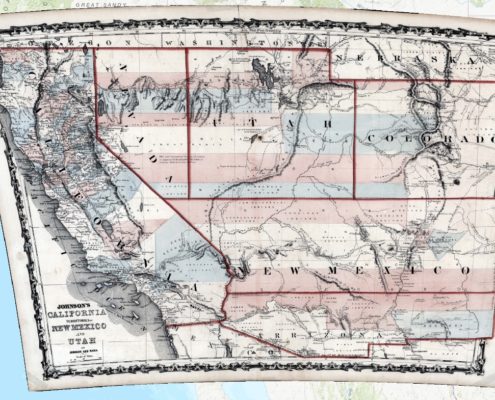
How Arizona got its almost-square shape west of New Mexico
A fascinating website, “How Did Arizona Get its Shape?,” shows that continental expansion in North America led to armed conflicts with Native American groups. Collectively known as the American Indian Wars, the conflicts began in the 1600s,…

Use the proper Wi-Fi cable for best quality of service
A friend insists that “the Internet is down” whenever he can’t get a strong wireless connection on his smartphone. With that type of logic, enjoy this photo found on the afore-mentioned Internet:
“Wi-Fi” is apparently now synonymous…

No more mansplaining: Commandments for clergy – and all lay leaders
"Thou shalt not refer winkingly to my taking off my robe after worship as disrobing." A powerful essay by Pastor Melissa Florer-Bixler, “10 commandments for male clergy,” highlights the challenges that female clergy endure in a patriarchal…

Digital security tradeoffs often mean hard choices
It’s all about the tradeoffs! You can have the chicken or the fish, but not both. You can have the big engine in your new car, but that means a stick shift—you can’t have the V8 and an automatic. Same for that cake you want to have and eat.…
OWASP and mainframe articles for Enterprise.nxt Insights did quite well
I’m #1! Well, actually #4 and #7. During 2017, I wrote several article for Hewlett Packard Enterprise’s online magazine, Enterprise.nxt Insights, and two of them were quite successful – named as #4 and #7 in the site’s list of Top 10…

The future tech user-interface: It’s all about speech
Amazon says that that a cloud-connected speaker/microphone was at the top of the charts: “This holiday season was better than ever for the family of Echo products. The Echo Dot was the #1 selling Amazon Device this holiday season, and the…

Malware damages Android phones. Are IoT devices next?
Software can affect the performance of hardware. Under the right (or wrong) circumstances, malware can cause the hardware to become physically damaged – as the cyberattack on Iran’s centrifuges provided in 2010, and which an errant coin-mining…

Get ready for Man-in-the-Middle (MITM) cyberattacks
Man-in-the-Middle (MITM or MitM) attacks are about to become famous. Famous, in the way that ransomware, Petya, Distributed Denial of Service (DDoS), and credit-card skimmers have become well-known.
MITM attacks go back thousands of years.…

Updating the Scrum agile process for 2017
Agility – the ability to deliver projects quickly. That applies to new projects, as well as updates to existing projects. The agile software movement began when many smart people became frustrated with the classic model of development, where…

Payment cards and bill payment services are great for criminals
Criminals steal money from banks. Nothing new there: As Willie Sutton famously said, “I rob banks because that's where the money is.”
Criminals steal money from other places too. While many cybercriminals target banks, the reality is…

The FBI and Secret Service view of cyber criminals
Law enforcement officials play a vital role tracking down and neutralizing cyber criminals. Theirs is a complex, often thankless, mission. Here are some insights shared by two current, and one former, high-level officials from U.S. law enforcement,…

Scammers warn you to ignore other scams, focus on their scams instead
Isn’t this rich? I get these occasionally and they always elicit a chuckle, especially when they refer to “mafias.” Don’t reply to these emails. Delete them instead.
From: "Mrs. CYNDY BANKSl" email hidden; JavaScript is required
Date: December 4, 2017…

Scam email claims your credit card will be charged – don’t open the attachment
I’ve seen a flurry of these messages recently; by a flurry, I mean 34 in the past two days. The emails come with a variety of texts on the same theme, with randomized “from” email addresses, sender names, salutations, credit-card brand…
