 What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter.
What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter.
Sadly, fighting back smarter isn’t always the case. At least, not when looking over the vendor offerings at RSA Conference 2017, held mid-February in San Francisco. Sadly, some of the products and services wouldn’t have seemed out of place a decade ago. Oh, look, a firewall! Oh look, a hardware device that sits on the network and scans for intrusions! Oh, look, a service that trains employees not to click on phishing spam!
Fortunately, some companies and big thinkers are thinking new about the types of attacks… and the best ways to protect against them, detect when those protections end, how to respond when attacks are detected, and ways to share information about those attacks.
The battle, after all, is asymmetric. Think about your typical target: It’s a business or a government organization or a military or a person. It is known. It can be identified. It can’t hide, or it can’t hide for long. It defenses, or at least their outer perimeter, can be seen and tested. Security secrets and vulnerabilities can be neutralized by someone who spills those secrets, whether through spying or social engineering.
Knowing the enemy
By contrast, while attackers know who the target is, the target doesn’t know who the attackers are. There many be many attackers, and they can shift targets on short notice, going after the biggest prize or the weakest prize. They can swamp the target with attacks. If one attackers is neutralized, the other attackers are still a threat. And in fact, even the attackers don’t know who the other attackers are. Their lack of coordination is a strength.
In cyberwarfare, as in real warfare, a single successful incursion can have incredible consequences. With one solid foothold in an endpoint – whether that endpoint is on a phone or a laptop, on a server or in the cloud – the bad guys are in a good position to gain more intelligence, seek out credentials, undermine defenses, and take over new footholds.
A Failed Approach
The posture of the cybersecurity industry – and of info sec professionals and the CISO – must shift. For years, the focus was almost exclusively on prevention. Install a firewall, and keep that firewall up to date! Install antivirus software, and keep adding signatures! Install intrusion detection systems, and then upgrade them to intrusion prevention systems!
That approached failed, just as an approach to medicine that focus exclusively on wellness, healthy eating and taking vitamins will fail. The truth is that breaches happen, in part because organizations don’t do a perfect job with their prevention methods, and in part because bad guys find new weaknesses that nobody considered, from zero-day software vulnerabilities to clever new spearphishing techniques. A breach is inevitable, the industry has admitted. Now, the challenge is to detect that breach quickly, move swiftly to isolate the damage, and then identify root causes so that future attacks using that same vulnerability won’t succeed.
Meanwhile, threat intelligence tools allow businesses to share information, carefully and confidentially. When one company is attacked, others can learn how to guard against that same attack vector. Hey, criminals share information about vulnerabilities using the dark web – so let’s learn from their example.
At RSA Conference 2017, most of the messages were same-old, same-old. Not all, fortunately. I was delighted, however, to see a renewed emphasis at some companies, and in some keynotes, on innovation. Not merely to keep up with the competition or to realize short-term advantage of cybercriminals. But rather, continuous, long-term investment focused on the constantly changing nature of cybersecurity. Security thrives on innovation. Because the bad guys innovate too.
 Nothing you share on the Internet is guaranteed to be private to you and your intended recipient(s). Not on Twitter, not on Facebook, not on Google+, not using Slack or HipChat or WhatsApp, not in closed social-media groups, not via password-protected blogs, not via text message, not via email.
Nothing you share on the Internet is guaranteed to be private to you and your intended recipient(s). Not on Twitter, not on Facebook, not on Google+, not using Slack or HipChat or WhatsApp, not in closed social-media groups, not via password-protected blogs, not via text message, not via email.
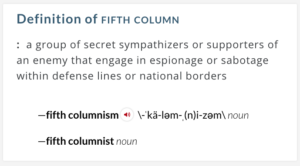 I can’t trust the Internet of Things. Neither can you. There are too many players and too many suppliers of the technology that can introduce vulnerabilities in our homes, our networks – or elsewhere. It’s dangerous, my friends. Quite dangerous. In fact, it can be thought of as a sort of Fifth Column, but not in the way many of us expected.
I can’t trust the Internet of Things. Neither can you. There are too many players and too many suppliers of the technology that can introduce vulnerabilities in our homes, our networks – or elsewhere. It’s dangerous, my friends. Quite dangerous. In fact, it can be thought of as a sort of Fifth Column, but not in the way many of us expected.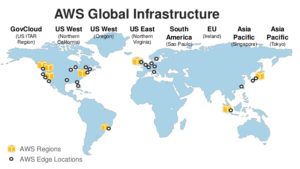 You keep reading the same three names over and over again. Amazon Web Services. Google Cloud Platform. Microsoft Windows Azure. For the past several years, that’s been the top tier, with a wide gap between them and everyone else. Well, there’s a fourth player, the IBM cloud, with their SoftLayer acquisition. But still, it’s AWS in the lead when it comes to Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS), with many estimates showing about a 37-40% market share in early 2017. In second place, Azure, at around 28-31%. Third, place, Google at around 16-18%. Fourth place, IBM SoftLayer, at 3-5%.
You keep reading the same three names over and over again. Amazon Web Services. Google Cloud Platform. Microsoft Windows Azure. For the past several years, that’s been the top tier, with a wide gap between them and everyone else. Well, there’s a fourth player, the IBM cloud, with their SoftLayer acquisition. But still, it’s AWS in the lead when it comes to Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS), with many estimates showing about a 37-40% market share in early 2017. In second place, Azure, at around 28-31%. Third, place, Google at around 16-18%. Fourth place, IBM SoftLayer, at 3-5%.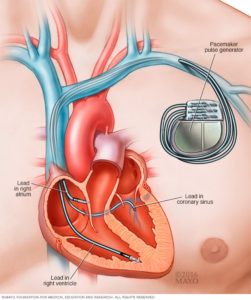 Modern medical devices increasingly leverage microprocessors and embedded software, as well as sophisticated communications connections, for life-saving functionality. Insulin pumps, for example, rely on a battery, pump mechanism, microprocessor, sensors, and embedded software. Pacemakers and cardiac monitors also contain batteries, sensors, and software. Many devices also have WiFi- or Bluetooth-based communications capabilities. Even hospital rooms with intravenous drug delivery systems are controlled by embedded microprocessors and software, which are frequently connected to the institution’s network. But these innovations also mean that a software defect can cause a critical failure or security vulnerability.
Modern medical devices increasingly leverage microprocessors and embedded software, as well as sophisticated communications connections, for life-saving functionality. Insulin pumps, for example, rely on a battery, pump mechanism, microprocessor, sensors, and embedded software. Pacemakers and cardiac monitors also contain batteries, sensors, and software. Many devices also have WiFi- or Bluetooth-based communications capabilities. Even hospital rooms with intravenous drug delivery systems are controlled by embedded microprocessors and software, which are frequently connected to the institution’s network. But these innovations also mean that a software defect can cause a critical failure or security vulnerability. Think about alarm systems in cars. By default, many automobiles don’t come with an alarm system installed from the factory. That was for three main reasons: It lowered the base sticker price on the car; created a lucrative up-sell opportunity; and allowed for variations on alarms to suit local regulations.
Think about alarm systems in cars. By default, many automobiles don’t come with an alarm system installed from the factory. That was for three main reasons: It lowered the base sticker price on the car; created a lucrative up-sell opportunity; and allowed for variations on alarms to suit local regulations. Cloud-based firewalls come in two delicious flavors: vanilla and strawberry. Both flavors are software that checks incoming and outgoing packets to filter against access policies and block malicious traffic. Yet they are also quite different. Think of them as two essential network security tools: Both are designed to protect you, your network, and your real and virtual assets, but in different contexts.
Cloud-based firewalls come in two delicious flavors: vanilla and strawberry. Both flavors are software that checks incoming and outgoing packets to filter against access policies and block malicious traffic. Yet they are also quite different. Think of them as two essential network security tools: Both are designed to protect you, your network, and your real and virtual assets, but in different contexts. What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter.
What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter. Everyone has received those crude emails claiming to be from your bank’s “Secuirty Team” that tells you that you need to click a link to “reset you account password.” It’s pretty easy to spot those emails, with all the misspellings, the terrible formatting, and the bizarre “reply to” email addresses at domains halfway around the world. Other emails of that sort ask you to review an unclothed photo of a A-list celebrity, or open up an attached document that tells you what you’ve won.
Everyone has received those crude emails claiming to be from your bank’s “Secuirty Team” that tells you that you need to click a link to “reset you account password.” It’s pretty easy to spot those emails, with all the misspellings, the terrible formatting, and the bizarre “reply to” email addresses at domains halfway around the world. Other emails of that sort ask you to review an unclothed photo of a A-list celebrity, or open up an attached document that tells you what you’ve won. What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off.
What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off.