 Software can affect the performance of hardware. Under the right (or wrong) circumstances, malware can cause the hardware to become physically damaged – as the cyberattack on Iran’s centrifuges provided in 2010, and which an errant coin-mining malware is demonstrating right now. Will intentional or unintentional damage to IoT devices be next?
Software can affect the performance of hardware. Under the right (or wrong) circumstances, malware can cause the hardware to become physically damaged – as the cyberattack on Iran’s centrifuges provided in 2010, and which an errant coin-mining malware is demonstrating right now. Will intentional or unintentional damage to IoT devices be next?
Back in late 2009 and early 2010, a computer worm labeled Stuxnet targeted the centrifuges used by Iran to refine low-grade nuclear material into weapons-class materials. The Stuxnet worm, which affected more than 200,000 machines, was estimated to physically damage 1,000 centrifuges.
How did it work? The Stuxnet virus checked to see if it was running on the right type of machine (i.e., a centrifuge of the specific type used by Iran), and if so, says Wikipedia:
The worm worked by first causing an infected Iranian IR-1 centrifuge to increase from its normal operating speed of 1,064 hertz to 1,410 hertz for 15 minutes before returning to its normal frequency. Twenty-seven days later, the worm went back into action, slowing the infected centrifuges down to a few hundred hertz for a full 50 minutes. The stresses from the excessive, then slower, speeds caused the aluminum centrifugal tubes to expand, often forcing parts of the centrifuges into sufficient contact with each other to destroy the machine.
From centrifuges to coin mining
The Stuxnet attacks were subtle, specific, and intentional. By contrast, the Loapi malware, which appeared in December 2017, appears to cause its damage inadvertently. Loapi, discovered by Kaspersky Labs, installs itself on Android devices using administrator privileges, and then does several nasty things, including displaying ads, acting as a zombie for distributed denial-of-service (DDoS) attacks, and mining Monero crypto-coin tokens.
The problem is that Loapi is a little too enthusiastic. When mining coins, Loapi works so hard that the phone overheats – and cooks the devices. Whoops. Says Neowin.net:
In its test, the firm found that after just two days, the constant load from mining caused its test phone’s battery to bulge, which also deformed the phone’s outer shell. This last detail is quite alarming, as it has the potential to cause serious physical harm to affected handset owners.
Damaging the Internet of Things
If malware gets onto an IoT device… who knows what it could do? Depending on the processor, memory, and network connectivity, some IoT devices could be turned into effective DDoS zombies or digital coin miners. Network security cameras have already been infected by spyware, so why not zombieware or miningware? This could be a significant threat for plug-in devices that are not monitored closely, and which contain considerable CPU power. Imagine a point-of-sale kiosk that also mined Bitcoin.
The possibility of damage is a reality, as is shown by Loapi. It’s possible that malware could somehow damage the device inadvertently, perhaps by messing up the firmware and bricking the machine, or by overloading the processor and memory to the point where it overwhelms on-board cooling mechanisms.
Then there’s the potential for intentional damage of IoT devices, either in a large scale or targeting a specific organization. This could be leveraged for extortion by criminal gangs, or for the destruction of public infrastructure or private enterprise by cyberterrorists or state-sponsored actors. If the creators of Stuxnet could damage centrifuges nearly a decade ago, it’s a sure bet that researchers are working on other attacks of that sort. It’s a sobering thought.

 Man-in-the-Middle (MITM or MitM) attacks are about to become famous. Famous, in the way that ransomware, Petya, Distributed Denial of Service (DDoS), and credit-card skimmers have become well-known.
Man-in-the-Middle (MITM or MitM) attacks are about to become famous. Famous, in the way that ransomware, Petya, Distributed Denial of Service (DDoS), and credit-card skimmers have become well-known. Agility – the ability to deliver projects quickly. That applies to new projects, as well as updates to existing projects. The agile software movement began when many smart people became frustrated with the classic model of development, where first the organization went through a complex process to develop requirements (which took months or years), and wrote software to address those requirements (which took months or years, or maybe never finished). By then, not only did the organization miss out on many opportunities, but perhaps the requirements were no longer valid – if they ever were.
Agility – the ability to deliver projects quickly. That applies to new projects, as well as updates to existing projects. The agile software movement began when many smart people became frustrated with the classic model of development, where first the organization went through a complex process to develop requirements (which took months or years), and wrote software to address those requirements (which took months or years, or maybe never finished). By then, not only did the organization miss out on many opportunities, but perhaps the requirements were no longer valid – if they ever were. Criminals steal money from banks. Nothing new there: As Willie Sutton famously said, “I rob banks because that’s where the money is.”
Criminals steal money from banks. Nothing new there: As Willie Sutton famously said, “I rob banks because that’s where the money is.” Law enforcement officials play a vital role tracking down and neutralizing cyber criminals. Theirs is a complex, often thankless, mission. Here are some insights shared by two current, and one former, high-level officials from U.S. law enforcement, who spoke at the
Law enforcement officials play a vital role tracking down and neutralizing cyber criminals. Theirs is a complex, often thankless, mission. Here are some insights shared by two current, and one former, high-level officials from U.S. law enforcement, who spoke at the  Isn’t this rich? I get these occasionally and they always elicit a chuckle, especially when they refer to “mafias.” Don’t reply to these emails. Delete them instead.
Isn’t this rich? I get these occasionally and they always elicit a chuckle, especially when they refer to “mafias.” Don’t reply to these emails. Delete them instead.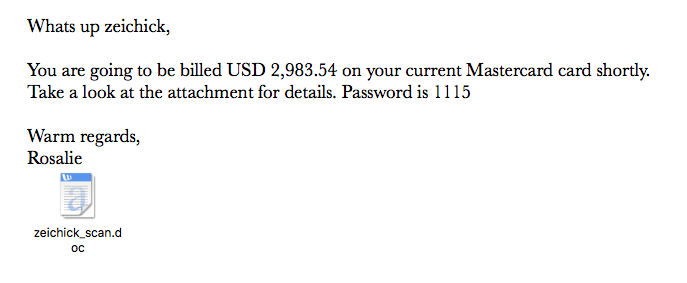 The common element: An email attachment. It’s a corrupted Microsoft Word document that contains nasty malware that will do bad things to your computer. (The bad things vary depending which versions of Microsoft Word you have installed.) Don’t open it!
The common element: An email attachment. It’s a corrupted Microsoft Word document that contains nasty malware that will do bad things to your computer. (The bad things vary depending which versions of Microsoft Word you have installed.) Don’t open it! If you see messages like this, delete them. Don’t respond. Never open attachments from messages if you don’t know and trust the sender… and even then, be wary.
If you see messages like this, delete them. Don’t respond. Never open attachments from messages if you don’t know and trust the sender… and even then, be wary.