Z Trek: The Alan Zeichick Weblog

Celebrate the 20th anniversary of SD Times!
February 23, 2000 — the debut issue of SD Times
hit the stands and changed my world. Launched as a printed semi-monthly
newspaper in tabloid size, SD Times grew into the world’s leading
publication for software development managers.
Ted…

Read the top CISO priorities for 2020
David McLeod, Cox Enterprises
“Training and recovery.” That’s where David McLeod,
chief information security officer of Cox Enterprises, says that CISOs should
spend their money in 2020.
Training often focuses on making employees…

My exciting new job: Editor-in-Chief of Java Magazine
Java Magazine home page
I'm back in the saddle again, if by "saddle" you mean editing a magazine. Today, I took over the helm of Oracle's Java Magazine, one of the world's leading publications for software developers, with about 260,000…
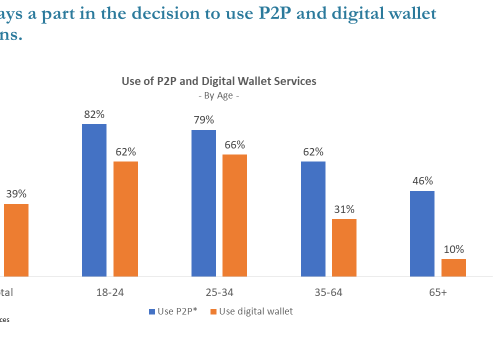
P2P payments go mainstream, and I am referenced
I was written about in “P2P Payments Go Mainstream in Canada,” by Pete Reville in PaymentsJournal:
One of the biggest hurdles in the adoption of mobile payments is consumer comfort. That is to say, in order for consumers to adopt digital…

Canadians love digital payments, cash not so much
Like
consumers and merchants all around the world, Canadians have embraced digital
payments instead of cash and checks. The growth rate is staggering, as
evidenced by statistics provided by Interac, which processes many of those
payments.
Digital…

Unlock the power of “yes” to drive creativity and innovation
Duncan Wardle
Next time you hear a bad idea in the office, try saying
“Yes.” That is, fight that impulse to say, “No, and here’s why your idea
isn’t going to work.” That negative response shuts down creativity, says Duncan J.…

Global charity CARE is bigger than CARE packages
Where will
you find CARE? Think of trouble spots around the
world where there are humanitarian disasters tied to extreme poverty, conflict,
hunger, or a lack of basic healthcare or education. CARE is on the ground in
these places,…

Linking on-prem data with cloud apps without moving many bytes
Solve the
puzzle: A company’s critical customer data is in a multiterabyte
on-premises database, and the digital marketing application that uses that data
to manage and execute campaigns runs in the cloud. How can the cloud-based
marketing…

Keep server apps running during patches with Oracle Autonomous Linux
When a
microprocessor vulnerability rocked the tech industry last year, companies
scrambled to patch nearly every server they had. In Oracle’s
case, that meant patching the operating system on about 1.5 million Linux-based
servers.
Oracle…

FedRAMP provides on-ramp to standardized government cloud computing
Phoenix City Hall
U.S.
government agencies needing high levels of information security can upgrade to
use the latest cloud technologies to run their applications. That’s thanks
to a pair of new cloud infrastructure regions from…

Thinking about security for houses of worship
It’s been a tough year, and security is on the mind of everyone
in the religious community, including synagogues, churches, and mosques.
Here’s a timely story in the Jewish News, a newspaper in the greater Phoenix
area: “Security
experts…

You can’t secure what you can’t see
My short essay, “You can’t secure what you can’t see,” was published in the 2019/2020 edition of Commerce Trends, from Manhattan Associates (page 18). The essay begins with,
When your company’s name appears in the press, the…

Trust your software developers, but also verify
Wayne Rash
A
talented programmer is a valued asset to any organization. But that doesn't mean you
shouldn't take steps to protect yourself and your organization, writes Wayne Rash in his new article for PC Magazine,
“Protect
Your Business…

The human-error side of cybersecurity
Want better
enterprise cybersecurity? It may seem counter-intuitive, but the answer
probably isn’t a surge in employee training or hiring of cybersecurity talent.
That’s because humans will always make errors, and humans can’t cope…

It’s time to log some miles with Enterprise.nxt Magazine
The editors of Enterprise.nxt wanted to publish one of my photos to illustrate their article, “Geek spotting: 3 ways to recognize a tech geek in the wild.” Yeah, it’s a photo of yours truly driving around in his Mazda Miata alongside…

Tech makes sailing more fun and engaging
I was pleased to contribute to a nice sport-technology story published in Mirage News, “Oracle Applies Cutting-Edge Tech to Enhance Fan Experiences.” My part begins like this:
Racing space-age yachts in San Francisco Bay (or anywhere)…

Charles Nutter: a Java programmer blown away by Ruby
Charles
Nutter remembers when, working as a Java architect, he attended a conference
and saw the Ruby programming language for the first
time. And he was blown away. “I was just stunned that I understood
every piece of code,…

Doug Cutter is the tall guy in Hadoop and Big Data
Doug Cutting stands head-and-shoulders above most developers I’ve met—figuratively, as well as literally. As one of the founders of the Hadoop open source project, which allows many Big Data projects to scale to handle huge problems…

Embed AI into applications for the biggest impact
Consider an employee
who normally fills out his weekly time card on Thursday afternoon, because he
doesn’t work most Fridays. Machine learning that’s built into a payroll application
could help the app learn the individual working habits…

I am wanted, dead or alive
This long missive is the best spam scam this month: Am I dead or alive? My urgen [sic] attention is needed. Because if I’m dead, they can’t scam me, right? Don’t reply to messages like this; just delete them. Even if they need courage.
From:…
Totally legit to send the new accountant my bank details
They’ve got overdue invoices to pay me. Don’t you think so? Uh, no. Don’t send people like this your bank info – or anything. Delete such scam messages, don’t reply to them.
From: email hidden; JavaScript is required
Subject: RE: Overdue Invoices
To:…

Name that out-of-tune song for the win
Can you name that Top 40 pop song in 10 seconds? Sure, that sounds easy. Can you name that pop song—even if it’s played slightly out of tune? Uh oh, that’s a lot harder. However, if you can guess 10 in a row, you might share in a cash…

New Mexico’s high degree of blockchain
Every new graduate from Central New Mexico Community College leaves school with a beautiful paper diploma covered in fine calligraphy, colorful seals, and official signatures. This summer, every new graduate also left with the same information…

Thank you “Gavin” for the SEO spam
Does “Gavin” seem totally above-board to you? Don’t you want what his real name is? No matter what, it’s a scam. That he tried to bypass my spam filter by spoofing my own email address in the “from” header is a nice touch. And doesn't…

Exploring the autonomous features in the Oracle Autonomous Database
Oracle Database is the world’s most popular enterprise database. This year’s addition of autonomous operating capabilities to the cloud version of Oracle Database is one of the most important advances in the database’s history. What does…
Chatbots meet education at the University of Adelaide
In Australia, at 8 a.m. on ‘Results Day,’ thousands and thousands of South Australian year 12 students receive their ATAR (Australia Tertiary Admissions Rank)—the all-important standardized score used to gain admission to universities…

The scammer has a modesty obligation
This seems legit... Not. What made it worth sharing was the opening, “It’s my modesty obligation…” It’s that obligation that will ensure the hitch free transfer of our fund, of course. That doesn’t explain why someone at the United…

All aboard the express train to the cloud
“All aboooooaaaaard!” Whether you love to watch the big freight engines rumble by, or you just ride a commuter train to work, the safety rules around trains are pretty simple for most of us. Look both ways before crossing the track, and never try…

Knowledge requires context
Knowledge is power—and knowledge with the right context at the right moment is the most powerful of all. Emerging technologies will leverage the power of context to help people become more efficient, and one of the first to do so is a new…

Hackers want your data columns — not your data rows
At too many government agencies and companies, the security mindset, even though it’s never spoken, is that “We’re not a prime target, our data isn’t super-sensitive.” Wrong. The reality is that every piece of personal data adds to…
