
February 23, 2000 — the debut issue of SD Times hit the stands and changed my world. Launched as a printed semi-monthly newspaper in tabloid size, SD Times grew into the world’s leading publication for software development managers.
Ted Bahr and I formed BZ Media in mid-1999. SD Times was the first of our many publications, conferences, and websites, all B2B for the technology industry. Today, SD Times flourishes as part of D2 Emerge, and we couldn’t be more proud to see our beloved SD Times continue to serve this important audience.
Let’s look back. David Rubinstein — who started out as executive editor of SD Times and is now co-owner of D2 Emerge and editor-in-chief of the magazine — put out a great 20th anniversary issue. (The other D is Dave Lyman.)
The special issue includes essays from me (page 18) and from Ted (page 12). Dave wrote a remembrance column (page 46) and art director Mara Leonardi shares some of her favorite SD Times covers and images (page 20).
Click here to read the anniversary issue or download it as a PDF.
Meanwhile, my favorite part of the special 20th anniversary issues are the old photos.
- There’s one of Ted and Alan, doing our silly “‘I’m the B’ and ‘I’m the Z’” schtick based on Saturday Night Live’s Hans und Franz.
- There’s one of the crazy launch crew celebrating the release of the first issue.
- There’s one of BZ Media employees standing in the water for some unknown reason.
- There’s a lot of alcohol being consumed. That’s what happens when your offices are next to a bar.
I love those people, and miss working with every single one of them. Thank you, Ted, Dave, Dave, Mara, Erzi, Eddie, Viena, Pat, Rebecca, Erin, Katie, Alex, Whitney, Adam, Stacy, Yvonne, Christina, Jon, Paula, David, Craig, Marilyn, Robin, LuAnn, Julie, Charlie, PJ, Lindsey, Agnes, Victoria, Catherine, Sabrina, Kathy, Jennifer, Jeff, Brenner, Doug, Dan, Lisa, Brian, Michele, Polina, Anne, Suzanne, Ryan, Jeanie, Josette, Debbie, Michelle, Nicole, Greg, Usman, Robert, Robbie, and so many others for making SD Times and BZ Media a success. Those were among the best years of my life.









 “Ransomware! Ransomware! Ransomware!” Those words may lack the timeless resonance of Steve Ballmer’s epic “
“Ransomware! Ransomware! Ransomware!” Those words may lack the timeless resonance of Steve Ballmer’s epic “

 As many of you know, I am co-founder and part owner of BZ Media LLC. Yes, I’m the “Z” of BZ Media. Here is exciting news released today about one of our flagship events, InterDrone.
As many of you know, I am co-founder and part owner of BZ Media LLC. Yes, I’m the “Z” of BZ Media. Here is exciting news released today about one of our flagship events, InterDrone. What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter.
What’s the biggest tool in the security industry’s toolkit? The patent application. Security thrives on innovation, and always has, because throughout recorded history, the bad guys have always had the good guys at the disadvantage. The only way to respond is to fight back smarter. What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off.
What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off. Want to open up your eyes, expand your horizons, and learn from really smart people? Attend a conference or trade show. Get out there. Meet people. Have conversations. Network. Be inspired by keynotes. Take notes in classes that are delivering great material, and walk out of boring sessions and find something better.
Want to open up your eyes, expand your horizons, and learn from really smart people? Attend a conference or trade show. Get out there. Meet people. Have conversations. Network. Be inspired by keynotes. Take notes in classes that are delivering great material, and walk out of boring sessions and find something better. Are you a coder? Architect? Database guru? Network engineer? Mobile developer? User-experience expert? If you have hands-on tech skills, get those hands dirty at a Hackathon.
Are you a coder? Architect? Database guru? Network engineer? Mobile developer? User-experience expert? If you have hands-on tech skills, get those hands dirty at a Hackathon. Excellent story about SharePoint in ComputerWorld this week. It gives encouragement to those who prefer to run SharePoint in their own data centers (on-premises), rather than in the cloud. In “
Excellent story about SharePoint in ComputerWorld this week. It gives encouragement to those who prefer to run SharePoint in their own data centers (on-premises), rather than in the cloud. In “ Despite some recent progress, women are still woefully underrepresented in technical fields such as software development. There are many academic programs to bring girls into STEM (science, technology, engineering and math) at various stages in their education, from grade school to high school to college. Corporations are trying hard.
Despite some recent progress, women are still woefully underrepresented in technical fields such as software development. There are many academic programs to bring girls into STEM (science, technology, engineering and math) at various stages in their education, from grade school to high school to college. Corporations are trying hard. Today’s serendipitous discovery: A blog post about the Enterprise Software Development Conference (ESC), produced by
Today’s serendipitous discovery: A blog post about the Enterprise Software Development Conference (ESC), produced by  Forget vendor lock-in: Carrier operation support systems (OSS) and business support systems (BSS) are going open source. And so are many of the other parts of the software stack that drive the end-to-end services within and between carrier networks.
Forget vendor lock-in: Carrier operation support systems (OSS) and business support systems (BSS) are going open source. And so are many of the other parts of the software stack that drive the end-to-end services within and between carrier networks. San Francisco – Apple’s
San Francisco – Apple’s 
 Barcelona, Mobile World Congress 2016—IoT success isn’t about device features, like long-life batteries, factory-floor sensors and snazzy designer wristbands. The real power, the real value, of the Internet of Things is in the data being transmitted from devices to remote servers, and from those remote servers back to the devices.
Barcelona, Mobile World Congress 2016—IoT success isn’t about device features, like long-life batteries, factory-floor sensors and snazzy designer wristbands. The real power, the real value, of the Internet of Things is in the data being transmitted from devices to remote servers, and from those remote servers back to the devices.
 A hackathon – like the debut
A hackathon – like the debut 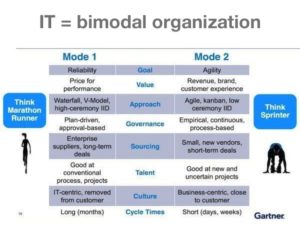 Las Vegas, December 2015 — Get ready for Bimodal IT. That’s the message from the
Las Vegas, December 2015 — Get ready for Bimodal IT. That’s the message from the  Drones are everywhere. Literally. My friend Steve, a wedding photographer, always includes drone shots. Drones are used by the military, of course, as well as spy agencies. They are used by public service agencies, like fire departments. By real estate photographers who want something better than Google Earth. By farmers checking on their fences. By security companies to augment foot patrols. And by Hollywood filmmakers, who
Drones are everywhere. Literally. My friend Steve, a wedding photographer, always includes drone shots. Drones are used by the military, of course, as well as spy agencies. They are used by public service agencies, like fire departments. By real estate photographers who want something better than Google Earth. By farmers checking on their fences. By security companies to augment foot patrols. And by Hollywood filmmakers, who  Washington, D.C. — “It’s not time to regulate and control and tax the Internet.” Those are words of wisdom about Net Neutrality from Dr. Robert Metcalfe, inventor of Ethernet, held here at the
Washington, D.C. — “It’s not time to regulate and control and tax the Internet.” Those are words of wisdom about Net Neutrality from Dr. Robert Metcalfe, inventor of Ethernet, held here at the  GOOGLE I/O 2004, SAN FRANCISCO — What is Android? It’s hard to know these days, and I’m not sure if that’s good or not. We all know what happened when Microsoft began seeing Windows as a common operating system for everything from embedded systems to desktops to phones to servers. By trying to be reasonably good at everything, Windows lost its way and ceased being the best platform for anything.
GOOGLE I/O 2004, SAN FRANCISCO — What is Android? It’s hard to know these days, and I’m not sure if that’s good or not. We all know what happened when Microsoft began seeing Windows as a common operating system for everything from embedded systems to desktops to phones to servers. By trying to be reasonably good at everything, Windows lost its way and ceased being the best platform for anything.