 “Ransomware! Ransomware! Ransomware!” Those words may lack the timeless resonance of Steve Ballmer’s epic “Developers! Developers! Developers!” scream in 2000, but ransomware was seemingly an obsession or at Black Hat USA 2017, happening this week in Las Vegas.
“Ransomware! Ransomware! Ransomware!” Those words may lack the timeless resonance of Steve Ballmer’s epic “Developers! Developers! Developers!” scream in 2000, but ransomware was seemingly an obsession or at Black Hat USA 2017, happening this week in Las Vegas.
There are good reason for attendees and vendors to be focused on ransomware. For one thing, ransomware is real. Rates of ransomware attacks have exploded off the charts in 2017, helped in part by the disclosures of top-secret vulnerabilities and hacking tools allegedly stolen from the United States’ three-letter-initial agencies.
For another, the costs of ransomware are significant. Looking only at a few attacks in 2017, including WannaCry, Petya, and NotPetya, corporates have been forced to revise their earnings downward to account for IT downtime and lost productivity. Those include Reckitt, Nuance, and FedEx. Those types of impact grab the attention of every CFO and every CEO.
Talking with another analyst at Black Hat, he observed that just about every vendor on the expo floor had managed to incorporate ransomware into its magic show. My quip: “I wouldn’t be surprised to see a company marketing network cables as specially designed to prevent against ransomware.” His quick retort: “The queue would be half a mile long for samples. They’d make a fortune.”
While we seek mezzanine funding for our Ransomware-Proof CAT-6 Cables startup, let’s talk about what organizations can and should do to handle ransomware. It’s not rocket science, and it’s not brain surgery.
- Train, train, train. End users will slip up, and they will click to open emails they shouldn’t open. They will visit websites they shouldn’t visit. And they will ignore security warnings. That’s true for the lowest-level trainee – and true for the CEO as well. Constant training can reduce the amount of stupidity. It can make a difference. By the way, also test your employees’ preparedness by sending out fake malware, and see who clicks on it.
- Invest in tools that can detect ransomware and other advanced malware. Users will make mistakes, and we’ve seen that there are some ransomware variants that can spread without user intervention. Endpoint security technology is required, and if possible, such tools should do more than passively warn end users if a problem is detected. There are many types of solutions available; look into them, and make sure there are no coverage gaps.
- Aggressively patch and update software. Patches existed for months to close the vulnerabilities exploited by the recent flurry of ransomware attacks. It’s understandable that consumers wouldn’t be up to date – but it’s inexcusable for corporations to have either not known about the patches, or to have failed to install them. In other words, these attacks were basically 100% avoidable. Maybe they won’t be in the future if the hackers exploit true zero-days, but you can’t protect your organization with out-of-date operating systems, applications, and security tools.
- Backup, backup, backup. Use backup technology that moves data security into the data center or into the cloud, so that ransomware can’t access the backup drive directly. Too many small businesses lost data on laptops, notebooks, and servers because there weren’t backups. We know better than this! By the way, one should assume that malware attacks, even ransomware, can be designed to destroy data and devices. Don’t assume you can write a check and get your data back safety.
- Stay up to date on threat data. You can’t rely upon the tech media, or vendor blogs, to keep you up to date with everything going on with cybersecurity. There are many threat data feeds, some curated and expensive, some free and lower-quality. You should find a threat data source that seems to fit your requirements and subscribe to it – and act on what you read. If you’re not going to consume the threat data yourself, find someone else to do so. An urgent warning about your database software version won’t do you any good if it’s in your trashcan.
Ransomware! Ransomware! Ransomware! When it comes to ransomware and advanced malware, it’s not a question of if, or even a question of when. Your organization, your servers, your network, your end-users, are under constant attack. It only takes one slip-up to wreak havoc on one endpoint, and potentially on multiple endpoints. Learn from what’s going on at Black Hat – and be ready for the worst.

 A major global cyberattack could cost US$53 billion of economic losses. That’s on the scale of a catastrophic disaster like 2012’s
A major global cyberattack could cost US$53 billion of economic losses. That’s on the scale of a catastrophic disaster like 2012’s 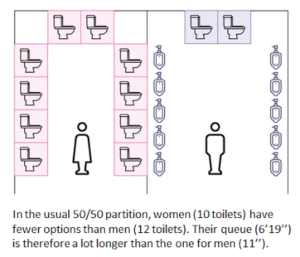 People Queue Magazine has a fascinating new article, “
People Queue Magazine has a fascinating new article, “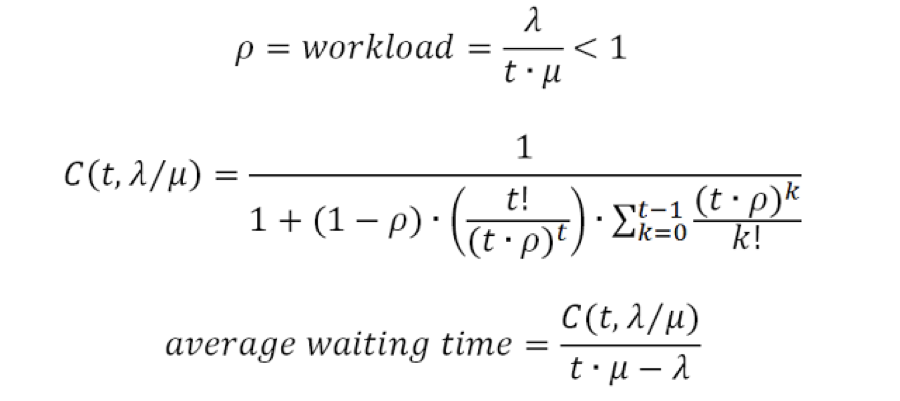

 Isn’t this exciting? Here’s an email received that promises me a significant payout ($620,000) for, well, am not really sure. I’m sure the scam would require paying some up-front fee and/or handing over bank account information. If you receive messages like this, simply delete them.
Isn’t this exciting? Here’s an email received that promises me a significant payout ($620,000) for, well, am not really sure. I’m sure the scam would require paying some up-front fee and/or handing over bank account information. If you receive messages like this, simply delete them.

 “Thou shalt not refer winkingly to my taking off my robe after worship as disrobing.” A powerful new essay by Pastor Melissa Florer-Bixler, “
“Thou shalt not refer winkingly to my taking off my robe after worship as disrobing.” A powerful new essay by Pastor Melissa Florer-Bixler, “ This is what Daffy Duck would describe as “dethpicable.” Absolutely deplorable.
This is what Daffy Duck would describe as “dethpicable.” Absolutely deplorable. General
General 
 While many would decry the system sexism and misogyny in cybersecurity, Ms. Brown sees opportunity:
While many would decry the system sexism and misogyny in cybersecurity, Ms. Brown sees opportunity: Did they tell their customers that data was stolen? No, not right away. When
Did they tell their customers that data was stolen? No, not right away. When  This is an amusing spam scam, if only because it’s so poorly written. Mr. Andrew McCabe, the Acting Director of the FBI, is certainly not behind this scam. Also, the FBI doesn’t send emails using Cyber Internet Services Private Ltd. in Pakistan, or refer people to Nigerian banks, or pay people via ATM card.
This is an amusing spam scam, if only because it’s so poorly written. Mr. Andrew McCabe, the Acting Director of the FBI, is certainly not behind this scam. Also, the FBI doesn’t send emails using Cyber Internet Services Private Ltd. in Pakistan, or refer people to Nigerian banks, or pay people via ATM card. It’s almost painful to see an issue of
It’s almost painful to see an issue of  Here are a few excerpts from one of the most important articles on leadership ever published. “
Here are a few excerpts from one of the most important articles on leadership ever published. “