 This is one of a series of articles I wrote for the monthly Bulletin of Peninsula Temple Sholom in Burlingame, Calif.
This is one of a series of articles I wrote for the monthly Bulletin of Peninsula Temple Sholom in Burlingame, Calif.
We were in trouble, and for a short time I thought my family’s lives were in danger. It was August 2004, and Carole, Michael, and I were on vacation in Palm Springs. With the temperature north of 110 degrees, we decided to skip the hotel’s swimming pool and take our 10-year-old son on a drive through nearby Joshua Tree National Park.
All went well until our car stalled and wouldn’t restart. What had been an Ultimate Driving Machine was now 3,500 pounds of inert steel. There wasn’t much shade, and of course we hadn’t brought nearly enough water with us.
Within a couple of hours, we were rescued by a AAA tow truck, and by the next day, our car was repaired. We were safe… but those hours in a rapidly heating metal box exchanged my trust in precision German engineering for appreciation of the awesome power of the Mohave Desert sun.
A car that runs. An air conditioner that blows cold air. A cell phone battery that is charged. Those are daily miracles that we take for granted… and we only notice them when we have a car that doesn’t work, an air conditioner that blows hot air, or a cell phone that has no charge or signal.
No cell signal? That’s a first-world problem. But our friends, family, and colleagues on the East Coast learned an even more important lesson about daily miracles after Hurricane Sandy. Power? Shelter? Heating? Phone? Broadband? A roof over your head? Some families couldn’t take those essentials for granted for days or weeks. Some families in New York and New Jersey still aren’t back in their homes.
Jewish values remind us of daily miracles, and implore us not to take them for granted. Many of us have been slightly grossed out during the Umafli La’asot prayer, the one that says, “With divine wisdom You have made our bodies, combining veins, arteries, and vital organs into a finely balanced network…”
When we get sick – when our vital organs don’t work right – we appreciate the daily miracles of our own existence.
We know that we have to maintain our cars, service our air conditioner, charge our phone batteries (and pay the wireless bill), eat healthfully, and visit our doctors.
Our synagogue is another daily miracle oft taken for granted. Too many of us, in today’s modern time, see Peninsula Temple Sholom as a place for adult ed. lectures, for b’nai mitzvah lessons, for hanging out with friends, for coming by on a Friday night for the yahrzeit of a loved one. When we need the shul, we come. When we don’t, those lovely buildings on Sebastian Drive don’t even enter our thoughts.
That’s too bad. Our synagogue is more than a place for drop-in programs and worship services. PTS is the moral center of our Judaism, the place for expressing our values, the heart of our community. Sure, we come by for a wedding, the Second Night Seder, to catch John Rothmann, or to educate our children – but the synagogue, and our hard-working clergy, staff, teachers, and volunteers have a bigger mission than to be a place for nice “Jewishy” programs.
Let me suggest that PTS is the AAA tow truck for our Jewish souls. When you need PTS, we are there for you. When you don’t need PTS, we are there for your friends and neighbors and our whole community. Believe me, there is no shortage of needs. And when you need PTS again, PTS is still there for you. Always.
That is why we need your support every year to sustain Peninsula Temple Sholom. In a typical year, the Temple has a budget of about $3.2 million. Where does that money come from? About $1.2 million comes from member dues, $1.3 million from Preschool tuition, and $200,000 from Religious School fees. That leaves about half a million dollars from sundry fees, building rentals… and mostly donations from you, our members.
Let’s talk about donations. Each fall, there is the High Holy Day Appeal. Thank you to all who contributed. Each spring, the fundraiser may take different forms. Last year, you may recall, we held the wonderful Erev Comedia with Rabbi Bob Alper. (This event not only supported the Temple, but I never laughed so hard in my life.)
This year, we are doing something new: an “unevent,” which is a straight-up request for donations dressed up like a party invitation. However, there’s no party, no raffle tickets, no silent auction, no live auction. This is a simple, no-gimmicks request for your financial support. Watch your mail for the “invitation,” laugh at the jokes – and please response to our appeal.
A beautiful prayer in Mishkan T’filah reads, “May the door of this synagogue be wide enough to receive all who hunger for love, all who are lonely for friendship. May it welcome all who have cares to unburden, thanks to express, hopes to nurture… May this synagogue be, for all who enter, the doorway to a richer and more meaningful life.”






 The
The  It has been proven, beyond any doubt whatsoever, that flame decals add 20-25 whp (wheel horsepower) to your vehicle, and of course even more bhp (brake horsepower). I know it’s proven because I read it on the Internet, and everything we read on the Internet is true, not #fakenews. Where did I read it?
It has been proven, beyond any doubt whatsoever, that flame decals add 20-25 whp (wheel horsepower) to your vehicle, and of course even more bhp (brake horsepower). I know it’s proven because I read it on the Internet, and everything we read on the Internet is true, not #fakenews. Where did I read it?  Think about alarm systems in cars. By default, many automobiles don’t come with an alarm system installed from the factory. That was for three main reasons: It lowered the base sticker price on the car; created a lucrative up-sell opportunity; and allowed for variations on alarms to suit local regulations.
Think about alarm systems in cars. By default, many automobiles don’t come with an alarm system installed from the factory. That was for three main reasons: It lowered the base sticker price on the car; created a lucrative up-sell opportunity; and allowed for variations on alarms to suit local regulations. It was our first-ever perp walk! My wife and I were on the way home from a quick grocery errand, and we were witnesses to and first responders to a nasty car crash. A car ran a red light and hit a turning vehicle head-on.
It was our first-ever perp walk! My wife and I were on the way home from a quick grocery errand, and we were witnesses to and first responders to a nasty car crash. A car ran a red light and hit a turning vehicle head-on. Mrs. Rachael Adams is back, and still wants to give me a fine Bavarian automobile. But is it a 7-series or a 5-series? Is it a 2015 or 2016 model? Doesn’t matter – it’s a scam. Just like the one a few weeks ago, also from Mrs. Adams, but at least that one was clearer about the vehicle. Hey, it’s the same reg code pin as last time, too. See “
Mrs. Rachael Adams is back, and still wants to give me a fine Bavarian automobile. But is it a 7-series or a 5-series? Is it a 2015 or 2016 model? Doesn’t matter – it’s a scam. Just like the one a few weeks ago, also from Mrs. Adams, but at least that one was clearer about the vehicle. Hey, it’s the same reg code pin as last time, too. See “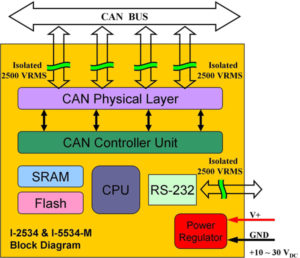 When it comes to cars, safety means more than strong brakes, good tires, a safety cage, and lots of airbags. It also means software that won’t betray you; software that doesn’t pose a risk to life and property; software that’s working for you, not for a hacker.
When it comes to cars, safety means more than strong brakes, good tires, a safety cage, and lots of airbags. It also means software that won’t betray you; software that doesn’t pose a risk to life and property; software that’s working for you, not for a hacker. Look what I fished out of my spam folder this morning. This is a variation on the usual lottery scam, and more enjoyable than most. But really, a
Look what I fished out of my spam folder this morning. This is a variation on the usual lottery scam, and more enjoyable than most. But really, a  I wrote five contributions for an ebook from AMD Developer Central — and forgot entirely about it! The book, called “
I wrote five contributions for an ebook from AMD Developer Central — and forgot entirely about it! The book, called “ Was it a software failure? The recent fatal crash of a Tesla in Autopilot mode is worrisome, but it’s too soon to blame Tesla’s software.
Was it a software failure? The recent fatal crash of a Tesla in Autopilot mode is worrisome, but it’s too soon to blame Tesla’s software. 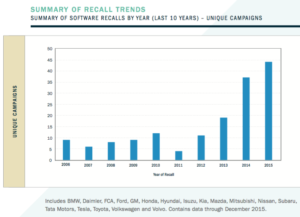
 Connected cars are vulnerable due to the radios that link them to the outside world. For example, consider cellular data links, such as the one in the Mercedes M-class SUV that my family owned for a while, allow for remote access to more than diagnostics: Using the system, called
Connected cars are vulnerable due to the radios that link them to the outside world. For example, consider cellular data links, such as the one in the Mercedes M-class SUV that my family owned for a while, allow for remote access to more than diagnostics: Using the system, called  I am hoovering directly from the blog of my friend
I am hoovering directly from the blog of my friend  GOOGLE I/O 2004, SAN FRANCISCO — What is Android? It’s hard to know these days, and I’m not sure if that’s good or not. We all know what happened when Microsoft began seeing Windows as a common operating system for everything from embedded systems to desktops to phones to servers. By trying to be reasonably good at everything, Windows lost its way and ceased being the best platform for anything.
GOOGLE I/O 2004, SAN FRANCISCO — What is Android? It’s hard to know these days, and I’m not sure if that’s good or not. We all know what happened when Microsoft began seeing Windows as a common operating system for everything from embedded systems to desktops to phones to servers. By trying to be reasonably good at everything, Windows lost its way and ceased being the best platform for anything. This is one of a series of articles I wrote for the monthly Bulletin of
This is one of a series of articles I wrote for the monthly Bulletin of  If there’s no news… well, let’s make some up. That’s my thought upon reading all the stories about Apple’s forthcoming iWatch – a product that, as far as anyone knows, doesn’t exist.
If there’s no news… well, let’s make some up. That’s my thought upon reading all the stories about Apple’s forthcoming iWatch – a product that, as far as anyone knows, doesn’t exist.


 Welcome to my blog. It has to start somewhere, and this is where it starts. And the trek had to start sometime; it should have started a long time ago, but it didn’t, so here we are.
Welcome to my blog. It has to start somewhere, and this is where it starts. And the trek had to start sometime; it should have started a long time ago, but it didn’t, so here we are.