 A little reverse psychology, eh? Don’t worry, trying to get this faux fortune will only cost you $450 from the spammers… or maybe more. Interesting that the name of the contact, Mr.James Richard, has the same spacing throughout, which is a telltale sign of either a bad copy/paste or a machine-generated form letter.
A little reverse psychology, eh? Don’t worry, trying to get this faux fortune will only cost you $450 from the spammers… or maybe more. Interesting that the name of the contact, Mr.James Richard, has the same spacing throughout, which is a telltale sign of either a bad copy/paste or a machine-generated form letter.
Delete messages like this; don’t reply to them.
From: “Mrs. CYNDY BANKS”
Subject: YOU ARE ADVISED TO STOP CONTACTING THEM!!!
Date: May 29, 2017 at 2:36:50 AM MST
Great News, YOU ARE ADVISED TO STOP CONTACTING THEM!!!
I am Mrs. CYNDY BANKS, I am a US citizen, 42 years Old. I reside here in Spring City, Pennsylvania. My residential address is as follows. 3663 Schuylkill Rd# 1, Spring City, Pennsylvania, United States, am thinking of relocating since I am now rich. I am one of those that took part in the Compensation in Troy Illinois many years ago and they refused to pay me, I had paid over $52,000 while in the United States trying to get my payment all to no avail.
I decided to travel down to Troy Illinois with all my compensation documents and i was directed to meet Mr.James Richard he is among the member of the COMPENSATION AWARD COMMITTEE, I contacted him and he explained everything to me. He said whoever is contacting us through emails are fake because the Inheritance/Compensation Law clearly states that the beneficiary/recipient is exempt from paying any out of pocket fees or charges to receive said funds.
Mr.James Richard took me to the paying bank for the claim of my Compensation payment. Right now I am the happiest woman on earth because I have received my compensation funds of $9,500,000.00 (nine million five hundred thousand dollars).
Moreover, Mr.James Richard showed me the full information of those that are yet to receive their payments and I saw your name and email address as one of the beneficiaries that is why I decided to email you to stop dealing with those people, they are not with your funds, they are only making money out of you. I will advise you to contact Mr.James Richard you have to contact him directly on this information below.
COMPENSATION AWARD HOUSE
Name: Mr.James Richard
Email:james.richard1155@gmail.com
Listed below are the name of mafias and banks behind the non release of your funds that I managed to sneak out for your kind perusal.
1) Prof. Charles soludo
2) Senator David Mark
2) Micheal Edward
3) Chief Joseph Sanusi
3) Sanusi Lamido
4) Dr. R. Rasheed
5) Mr. David Koffi
6) Barrister Awele Ugorji
7) Mr. Roland Ngwa
8) Barrister Ucheuzo Williams
9) Mr. Ernest Chukwudi Obi
10) Dr. Patrick Aziza Deputy Governor – Policy / Board Member
11) Mr. Tunde Lemo Deputy Governor – Financial Sector Surveillance/Board Member
12) Mrs. W. D. A. Mshelia Deputy Governor – Corporate Services / Board Members
13) Mrs. Okonjo Iweala
14) Mrs. Rita Ekwesili
15) Barr Jacob Onyema
16) Dr. Godwin Oboh: Director Union Bank Of Nigeria.
17) Mr. John Collins: Global Diplomat Director.
18) Foreign fund diplomatic courier
19) Barr. Becky Owens
20) Rev. Steven Jones
21) Mr. Alfred james
22) Mrs. Sherry Williams
23) Mr. Scott Larry
You really have to stop dealing with those people that are contacting you and telling you that your fund is with them, it is not in anyway with them, they are only taking advantage of you and they will dry you up until you have nothing. The only money I paid after I met Mr.James Richard was just $450 for the delivery charges, take note of that.
(NOTE: TELLING YOU TO PAY FOR ANY DELIVERY OR COURIER CHARGE IS ALL NOTHING BUT LIES, I REPEAT THE ONLY MONEY YOU WILL HAVE TO PAY AND WHICH I ALSO PAID IS $450 FOR THE DELIVERY CHARGES IMPOSED BY THE GOVERNMENT AND YOUR PACKAGE CONTAINING YOUR CERTIFIED BANK DRAFT CHEQUE WILL BE REACHING YOU THROUGH THE EXPRESS COURIER SERVICE).
Once again stop contacting those people, I will advise you to contact Mr.James Richard so that he can help you to deliver your funds instead of dealing with those liars that will be turning you around asking for different kind of money to complete your transaction.

 “Someone is waiting just for you / Spinnin’ wheel, spinnin’ true.”
“Someone is waiting just for you / Spinnin’ wheel, spinnin’ true.”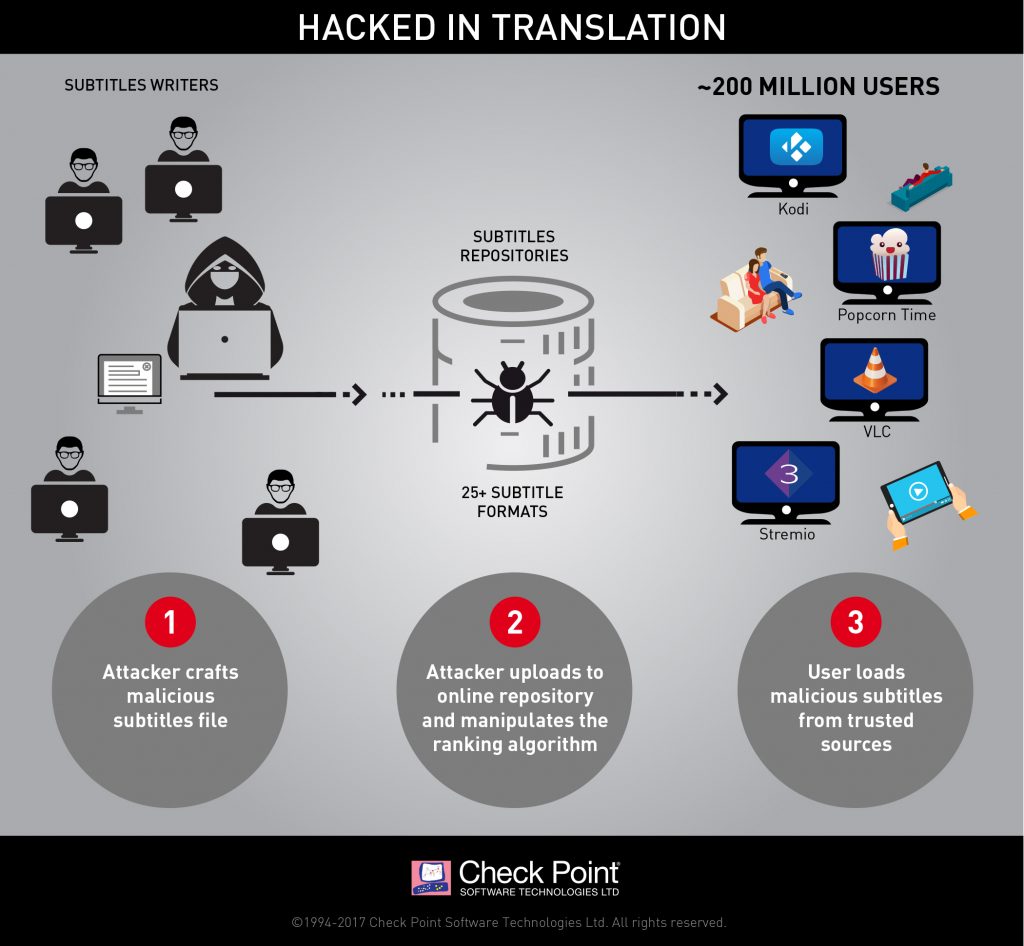
 March 2003: The U.S. International Trade Commission released a 32-page paper called, “
March 2003: The U.S. International Trade Commission released a 32-page paper called, “ According to a depressing story in Harvard Business Review, venture capitalists consider female entrepreneurs to be quite different than males. The perceived difference is not good. According to the May 17, 2017, story, “
According to a depressing story in Harvard Business Review, venture capitalists consider female entrepreneurs to be quite different than males. The perceived difference is not good. According to the May 17, 2017, story, “ From eWeek’s story, “
From eWeek’s story, “ Technical diligence starts when a startup or company has been approved for outside capital, but needs to be inspected to insure the value of the technology is “good enough” to accept investment. The average startup has something like 1/100 odds of receiving funding once they pitch a VC firm, which is why if investment is offered the ball shouldn’t be dropped during technical diligence. Most issues in technical diligence can be prevented. Since technical diligence is part of the investigation process to receiving venture capital, any business in theory could proactively prepare for technical diligence.
Technical diligence starts when a startup or company has been approved for outside capital, but needs to be inspected to insure the value of the technology is “good enough” to accept investment. The average startup has something like 1/100 odds of receiving funding once they pitch a VC firm, which is why if investment is offered the ball shouldn’t be dropped during technical diligence. Most issues in technical diligence can be prevented. Since technical diligence is part of the investigation process to receiving venture capital, any business in theory could proactively prepare for technical diligence.





 Many IT professionals were caught by surprise by last week’s huge cyberattack. Why? They didn’t expect ransomware to spread across their networks on its own.
Many IT professionals were caught by surprise by last week’s huge cyberattack. Why? They didn’t expect ransomware to spread across their networks on its own.
 Los informes llegaron rápidamente el viernes por la mañana, 12 de mayo – la primera vez que leí una alerta, referenciaba a docenas de hospitales en Inglaterra que fueron afectados por ransomware (sin darse cuenta que era ransomworm), negando a los médicos el acceso a los registros médicos de sus pacientes, causando demoras en cirujías y tratamientos en curso dijo la BBC,
Los informes llegaron rápidamente el viernes por la mañana, 12 de mayo – la primera vez que leí una alerta, referenciaba a docenas de hospitales en Inglaterra que fueron afectados por ransomware (sin darse cuenta que era ransomworm), negando a los médicos el acceso a los registros médicos de sus pacientes, causando demoras en cirujías y tratamientos en curso dijo la BBC,




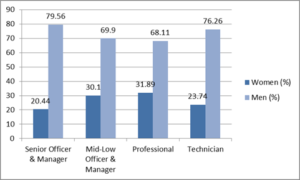 In the United States, Sunday, May 14, is Mother’s Day. (Mothering Sunday was March 27 this year in the United Kingdom.) This is a good time to reflect on the status of women of all marital status and family situations in information technology. The results continue to disappoint.
In the United States, Sunday, May 14, is Mother’s Day. (Mothering Sunday was March 27 this year in the United Kingdom.) This is a good time to reflect on the status of women of all marital status and family situations in information technology. The results continue to disappoint.
 I have a new research paper in Elsevier’s technical journal,
I have a new research paper in Elsevier’s technical journal,  To those who run or serve on corporate, local government or non-profit boards:
To those who run or serve on corporate, local government or non-profit boards: In 2016, Carnival Cruises was alleged to have laid off its entire 200-person IT department – and
In 2016, Carnival Cruises was alleged to have laid off its entire 200-person IT department – and  It has been proven, beyond any doubt whatsoever, that flame decals add 20-25 whp (wheel horsepower) to your vehicle, and of course even more bhp (brake horsepower). I know it’s proven because I read it on the Internet, and everything we read on the Internet is true, not #fakenews. Where did I read it?
It has been proven, beyond any doubt whatsoever, that flame decals add 20-25 whp (wheel horsepower) to your vehicle, and of course even more bhp (brake horsepower). I know it’s proven because I read it on the Internet, and everything we read on the Internet is true, not #fakenews. Where did I read it?