Malware in movie subtitles are coming to a mobile near you
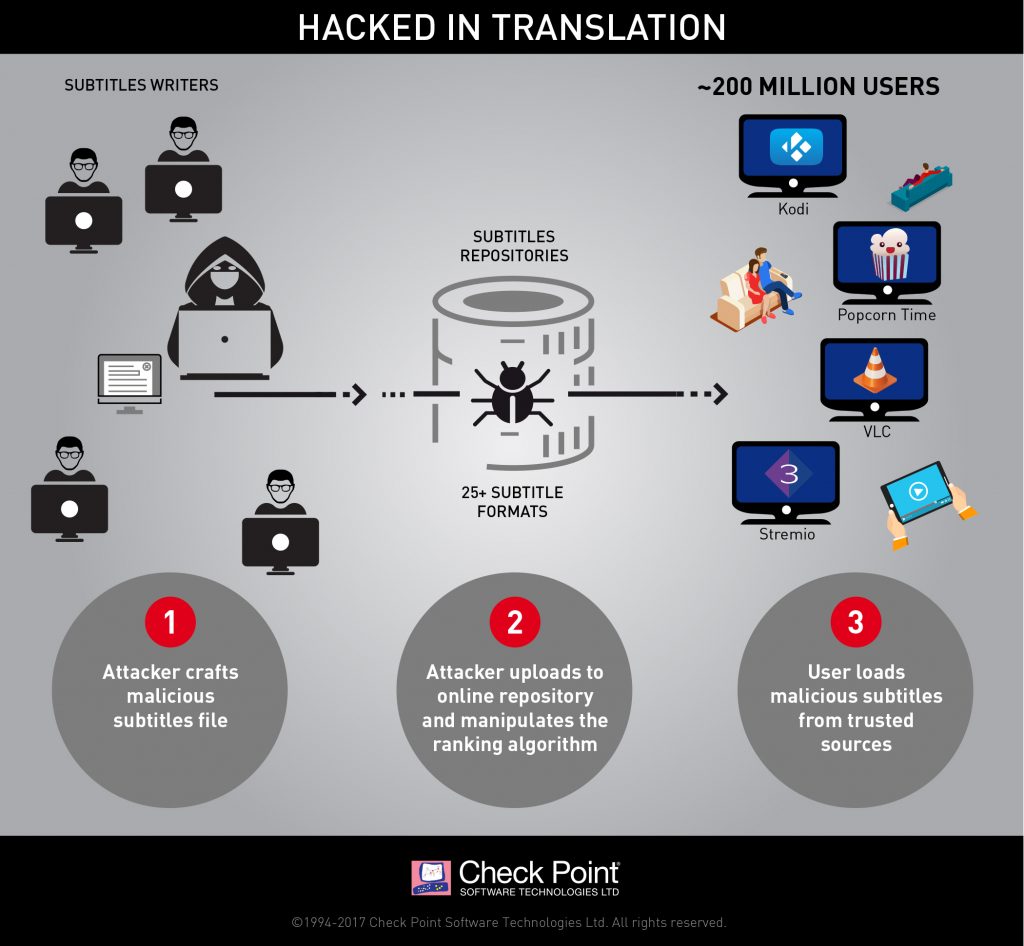
Movie subtitles — those are the latest attack vector for malware. According to Check Point Software, by crafting malicious subtitle files, which are then downloaded by a victim’s media player, attackers can take complete control over any type of device via vulnerabilities found in many popular streaming platforms. Those media players include VLC, Kodi (XBMC), Popcorn-Time and strem.io.
I was surprised to see that this would work, because I thought that text subtitles were just that – text. Silly me. Subtitles embedded into media files (like mp4 movies) can be encoded in dozens of different formats, each with unique features, capabilities, metadata, and payloads. The data and metadata in those subtitles can be hard to analyze, in part because of the many ways the subtitles are stored in a repository. To quote Check Point:
These subtitles repositories are, in practice, treated as a trusted source by the user or media player; our research also reveals that those repositories can be manipulated and be made to award the attacker’s malicious subtitles a high score, which results in those specific subtitles being served to the user. This method requires little or no deliberate action on the part of the user, making it all the more dangerous.
Unlike traditional attack vectors, which security firms and users are widely aware of, movie subtitles are perceived as nothing more than benign text files. This means users, Anti-Virus software, and other security solutions vet them without trying to assess their real nature, leaving millions of users exposed to this risk.
According to Check Point, more than 200 million users (or devices) are potentially vulnerable to this exploit. The risk?
Damage: By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.
Here’s an infographic from Check Point:
This type of vulnerability is reminiscent of steganography, where secret data is hidden inside image files. We have all become familiar with malicious macros, such as those hidden inside Microsoft Word .doc/.docx or Microsoft Excel .xls/.xlsx files. Those continue to become more sophisticated, even as antivirus or anti-malware scanners becomes more adept at detecting them. Similarly, executables and other malware can be hidden inside Adobe .pdf documents, or even inside image files.
Interestingly, sometimes that malware can be manually destroyed by format conversations. For example, you can turn a metadata-rich format into a dumb format. Turn a Word doc into rich text or plain text, and good-bye, malicious macro. Similarly, converting a malicious JPEG into a bitmap could wipe out any malware in the JPEG file’s header or footer. Of course, you’d lose other benefits as well, especially if there are benign or useful macros or metadata. That’s just how it goes.
See you at the movies!