 Tom Burns, VP and General Manager of Dell EMC Networking, doesn’t want 2018 to be like 2017. Frankly, none of us in tech want to hit the “repeat” button either. And we won’t, not with increased adoption of blockchain, machine learning/deep learning, security-as-a-service, software-defined everything, and critical enterprise traffic over the public Internet.
Tom Burns, VP and General Manager of Dell EMC Networking, doesn’t want 2018 to be like 2017. Frankly, none of us in tech want to hit the “repeat” button either. And we won’t, not with increased adoption of blockchain, machine learning/deep learning, security-as-a-service, software-defined everything, and critical enterprise traffic over the public Internet.
Of course, not all possible trends are positive ones. Everyone should prepare for more ransomware, more dangerous data breaches, newly discovered flaws in microprocessors and operating systems, lawsuits over GDPR, and political attacks on Net Neutrality. Yet, as the tech industry embraces 5G wireless and practical applications of the Internet of Things, let’s be optimistic, and hope that innovation outweighs the downsides of fast-moving technology.
Here, Dell has become a major force in networking across the globe. The company’s platform, known as Dell EMC Open Networking, includes a portfolio of data center switches and software, as well as solutions for campus and branch networks. Plus, Dell offers end-to-end services for digital transformation, training, and multivendor environment support.
Tom Burns heads up Dell’s networking business. That business became even larger in September 2106, which Dell closed on its US$67 billion acquisition of EMC Corp. Before joining Dell in 2012, Burns was a senior executive at Alcatel-Lucent for many years. He and I chatted in early January at one of Dell’s offices in Santa Clara, Calif.
Q: What’s the biggest tech trend from 2017 that you see continuing into 2018?
Tom Burns (TB): The trend that I think that will continue into 2018 and even beyond is around digital transformation. And I recognize that everyone may have a different definition of what that means, but what we at Dell Technologies believe it means is that the number of connected devices exploding, whether it be cell phones or RFIDs or intelligent type of devices that are looking at our factories and so forth.
And all of this information needs to be collected and analyzed, with what some call artificial intelligence. Some of it needs to be aggregated at the edge. Some of it’s going to be brought back to the core data centers. This is what we infer to as IT transformation, to enable workforce transformation and other capabilities to deliver the applications, the information, the video, the voice communications, in real time to the users and give them the intelligence from the information that’s being gathered to make real-time decisions or whatever they need the information for.
Q: What do you see as being the tech trend from 2017 that you hope won’t continue into 2018?
TB: The trend that won’t continue into 2018 is the old buying habits around previous-generation technology. CIOs and CEOs, whether in enterprises or in service providers, are going to have to think of a new way to deliver their services and applications on a real-time basis, and the traditional architectures that have driven our data centers over the years just is not going to work anymore. It’s not scalable. It’s not flexible. It doesn’t drive out the costs that are necessary in order to enable those new applications.
So one of the things that I think is going to stop in 2018 is the old way of thinking – proprietary applications, proprietary full stacks. I think disaggregation, open, is going to be adopted much, much faster.
Q: If you could name one thing that will predict how the tech industry will do business next year, what do you think it will be?
TB: Well, I think one of the major changes, and we’ve started to see it already, and in fact, Dell Technologies announced it about a year ago, is how is our technology being consumed? We’ve been, let’s face it, box sellers or even solution providers that look at it from a CapEx standpoint. We go in, talk to our customers, we help them enable a new application as a service, and we kind of walk away. We sell them the product, and then obviously we support the product.
More and more, I think the customers and the consumers are looking for different ways to consume that technology, so we’ve started things like consumption models like pay as you grow, pay as you turn on, consumption models that allows us to basically ignite new services on demand. We have some several customers that are doing this, particularly around the service provider area. So I think one way tech companies are going to change on how they deliver is this whole thing around pay as a service, consumption models and a new way to really provide the technology capabilities to our customers and then how do they enable them.
Q: If you could predict one thing that will change how enterprise customers do business next year…?
TB: One that we see as a huge, tremendous impact on how customers are going to operate is SD-WAN. The traditional way of connecting branches and office buildings and providing services to those particular branches is going to change. If you look at the traditional router, a proprietary architecture, dedicated lines, SD-WAN is offering a much lower cost but same level of service opportunity for customers to have that data center interconnectivity or branch connectivity, providing some of the services, maybe a full even office in the box, but security services, segmentation services, at a much lower cost basis. So I think that one of the major changes for enterprises next year and service providers is going to be this whole concept and idea with real technology behind it around Software-Defined WAN.
Read the full interview
There’s a lot more to my conversation with Tom Burns. Read the entire interview at Upgrade Magazine.


 In Australia, at 8 a.m. on ‘Results Day,’ thousands and thousands of South Australian year 12 students receive their ATAR (Australia Tertiary Admissions Rank)—the all-important standardized score used to gain admission to universities across Australia. The frustrating challenge: many are
In Australia, at 8 a.m. on ‘Results Day,’ thousands and thousands of South Australian year 12 students receive their ATAR (Australia Tertiary Admissions Rank)—the all-important standardized score used to gain admission to universities across Australia. The frustrating challenge: many are  “All aboooooaaaaard!” Whether you love to watch the big freight engines rumble by, or you just ride a commuter train to work, the safety rules around trains are pretty simple for most of us. Look both ways before crossing the track, and never try to beat a train, for example. If you’re a rail operator, however, safety is a much more complicated challenge—such as making sure you always have the right people on the right positions, and ensuring that the crew is properly trained, rested, and has up-to-date safety certifications.
“All aboooooaaaaard!” Whether you love to watch the big freight engines rumble by, or you just ride a commuter train to work, the safety rules around trains are pretty simple for most of us. Look both ways before crossing the track, and never try to beat a train, for example. If you’re a rail operator, however, safety is a much more complicated challenge—such as making sure you always have the right people on the right positions, and ensuring that the crew is properly trained, rested, and has up-to-date safety certifications.





 Software can affect the performance of hardware. Under the right (or wrong) circumstances, malware can cause the hardware to become physically damaged – as the cyberattack on Iran’s centrifuges provided in 2010, and which an errant coin-mining malware is demonstrating right now. Will intentional or unintentional damage to IoT devices be next?
Software can affect the performance of hardware. Under the right (or wrong) circumstances, malware can cause the hardware to become physically damaged – as the cyberattack on Iran’s centrifuges provided in 2010, and which an errant coin-mining malware is demonstrating right now. Will intentional or unintentional damage to IoT devices be next? The secret sauce is AI-based zero packet inspection. That’s how to secure mobile users, and their personal data and employers’ data.
The secret sauce is AI-based zero packet inspection. That’s how to secure mobile users, and their personal data and employers’ data. Smart televisions, talking home assistants, consumer wearables – that’s not the real story of the Internet of Things. While those are fun and get great stories on blogs and morning news reports, the real IoT is the Industrial IoT. That’s where businesses will truly be transformed, with intelligent, connected devices working together to improve services, reduce friction, and disrupt everything. Everything.
Smart televisions, talking home assistants, consumer wearables – that’s not the real story of the Internet of Things. While those are fun and get great stories on blogs and morning news reports, the real IoT is the Industrial IoT. That’s where businesses will truly be transformed, with intelligent, connected devices working together to improve services, reduce friction, and disrupt everything. Everything. Still no pastrami sandwich. Still no guinea pig. What’s the deal with the cigarette?
Still no pastrami sandwich. Still no guinea pig. What’s the deal with the cigarette? I am unapologetically mocking this company’s name.
I am unapologetically mocking this company’s name.  An organization’s Chief Information Security Officer’s job isn’t ones and zeros. It’s not about unmasking cybercriminals. It’s about reducing risk for the organization, for enabling executives and line-of-business managers to innovate and compete safely and securely. While the CISO is often seen as the person who loves to say “No,” in reality, the CISO wants to say “Yes” — the job, after all, is to make the company thrive.
An organization’s Chief Information Security Officer’s job isn’t ones and zeros. It’s not about unmasking cybercriminals. It’s about reducing risk for the organization, for enabling executives and line-of-business managers to innovate and compete safely and securely. While the CISO is often seen as the person who loves to say “No,” in reality, the CISO wants to say “Yes” — the job, after all, is to make the company thrive. “Someone is waiting just for you / Spinnin’ wheel, spinnin’ true.”
“Someone is waiting just for you / Spinnin’ wheel, spinnin’ true.”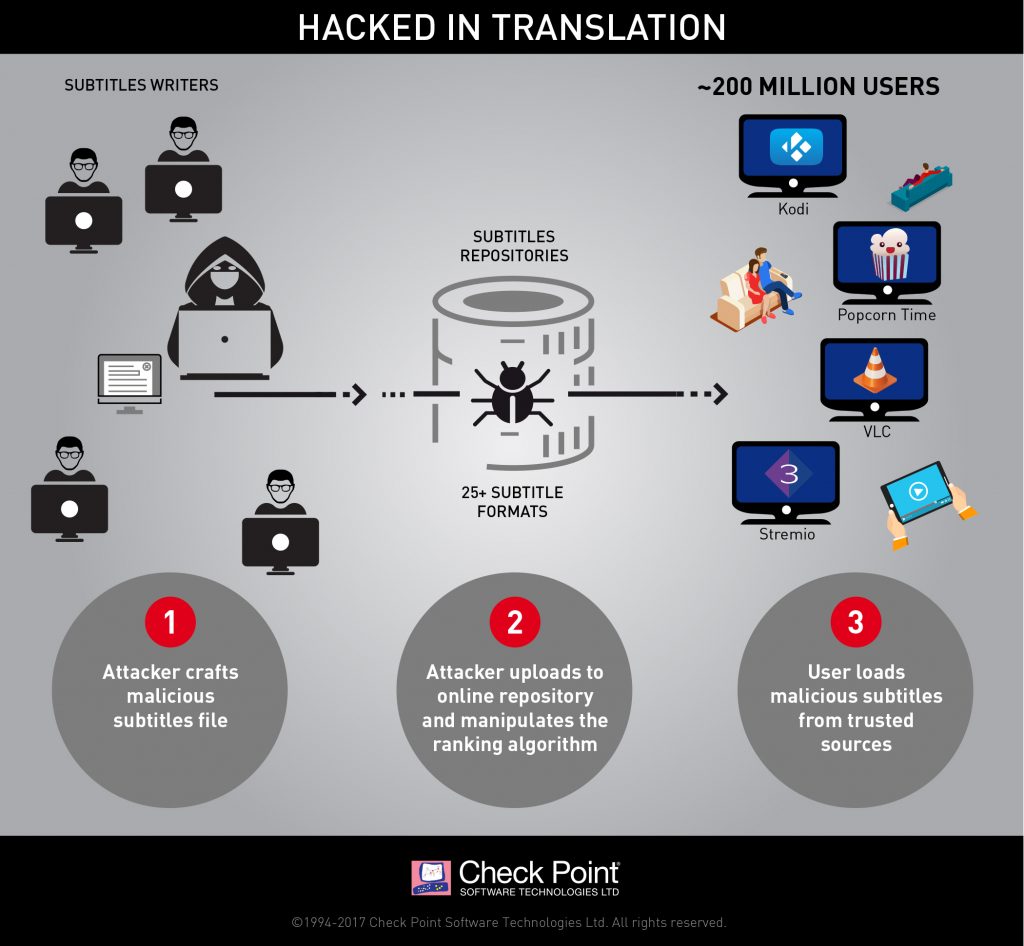
 From eWeek’s story, “
From eWeek’s story, “ Did you know that last year, 75% of data breaches were perpetrated by outsiders, and fully 25% involved internal actors? Did you know that 18% were conducted by state-affiliated actors, and 51% involved organized criminal groups?
Did you know that last year, 75% of data breaches were perpetrated by outsiders, and fully 25% involved internal actors? Did you know that 18% were conducted by state-affiliated actors, and 51% involved organized criminal groups? Wednesday, March 22, spreading from techie to techie. “Better change your iCloud password, and change it fast.” What’s going on?
Wednesday, March 22, spreading from techie to techie. “Better change your iCloud password, and change it fast.” What’s going on?  To absolutely nobody’s surprise, the U.S. Central Intelligence Agency can spy on mobile phones. That includes Android and iPhone, and also monitor the microphones on smart home devices like televisions.
To absolutely nobody’s surprise, the U.S. Central Intelligence Agency can spy on mobile phones. That includes Android and iPhone, and also monitor the microphones on smart home devices like televisions. “You walked 713 steps today. Good news is the sky’s the limit!”
“You walked 713 steps today. Good news is the sky’s the limit!” Cybercriminals want your credentials and your employees’ credentials. When those hackers succeed in stealing that information, it can be bad for individuals – and even worse for corporations and other organizations. This is a scourge that’s bad, and it will remain bad.
Cybercriminals want your credentials and your employees’ credentials. When those hackers succeed in stealing that information, it can be bad for individuals – and even worse for corporations and other organizations. This is a scourge that’s bad, and it will remain bad.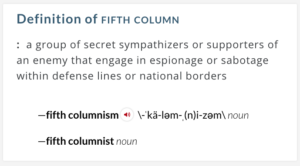 I can’t trust the Internet of Things. Neither can you. There are too many players and too many suppliers of the technology that can introduce vulnerabilities in our homes, our networks – or elsewhere. It’s dangerous, my friends. Quite dangerous. In fact, it can be thought of as a sort of Fifth Column, but not in the way many of us expected.
I can’t trust the Internet of Things. Neither can you. There are too many players and too many suppliers of the technology that can introduce vulnerabilities in our homes, our networks – or elsewhere. It’s dangerous, my friends. Quite dangerous. In fact, it can be thought of as a sort of Fifth Column, but not in the way many of us expected. What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off.
What’s on the industry’s mind? Security and mobility are front-and-center of the cerebral cortex, as two of the year’s most important events prepare to kick off. I was dismayed this morning to find an email from Pebble — the smart watch folks — essentially announcing their demise. The company is no longer a viable concern, says the message, and the assets of the company are being sold to Fitbit. Some of Pebble’s staff will go to Fitbit as well.
I was dismayed this morning to find an email from Pebble — the smart watch folks — essentially announcing their demise. The company is no longer a viable concern, says the message, and the assets of the company are being sold to Fitbit. Some of Pebble’s staff will go to Fitbit as well. From company-issued tablets to BYOD (bring your own device) smartphones, employees are making the case that mobile devices are essential for productivity, job satisfaction, and competitive advantage. Except in the most regulated industries, phones and tablets are part of the landscape, but their presence requires a strong security focus, especially in the era of non-stop malware, high-profile hacks, and new vulnerabilities found in popular mobile platforms. Here are four specific ways of examining this challenge that can help drive the choice of both policies and technologies for reducing mobile risk.
From company-issued tablets to BYOD (bring your own device) smartphones, employees are making the case that mobile devices are essential for productivity, job satisfaction, and competitive advantage. Except in the most regulated industries, phones and tablets are part of the landscape, but their presence requires a strong security focus, especially in the era of non-stop malware, high-profile hacks, and new vulnerabilities found in popular mobile platforms. Here are four specific ways of examining this challenge that can help drive the choice of both policies and technologies for reducing mobile risk. Are you a coder? Architect? Database guru? Network engineer? Mobile developer? User-experience expert? If you have hands-on tech skills, get those hands dirty at a Hackathon.
Are you a coder? Architect? Database guru? Network engineer? Mobile developer? User-experience expert? If you have hands-on tech skills, get those hands dirty at a Hackathon.