Z Trek: The Alan Zeichick Weblog

Modern programming lessons learned from 1970s mainframes
About a decade ago, I purchased a piece of a mainframe on eBay — the name ID bar. Carved from a big block of aluminum, it says “IBM System/370 168,” and it hangs proudly over my desk.
My time on mainframes was exclusively with the IBM…

DevOps is the future of enterprise software development, because cloud computing
To get the most benefit from the new world of cloud-native server applications, forget about the old way of writing software. In the old model, architects designed software. Programmers wrote the code, and testers tested it on test server. Once…
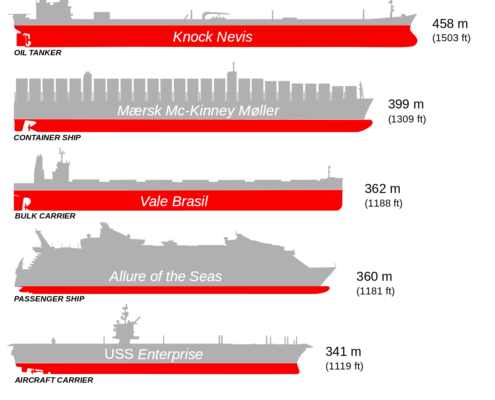
Sinking sensation: Protecting the Internet of Ships from cyberattack
Loose cyber-lips can sink real ship. According to separate reports published by the British government and the cruise ship industry, large cargo and passenger vessels could be damaged by cyberattacks – and potentially even sent to the bottom…

AI understands when servers have drifted into the danger zone
“One of these things is not like the others,” the television show Sesame Street taught generations of children. Easy. Let’s move to the next level: “One or more of these things may or may not be like the others, and those variances…

AOL Instant Messenger is almost dead, but we won’t miss AIM at all
AOL Instant Messenger will be dead before the end of 2017. Yet, instant messages have succeeded far beyond what anyone could have envisioned for either SMS (Short Message Service, carried by the phone company) or AOL, which arguably brought…

Lift and shift workloads, and create new apps, for the same cloud
IT managers shouldn’t have to choose between cloud-driven innovation and data-center-style computing. Developers shouldn’t have to choose between the latest DevOps programming using containers and microservices, and traditional architectures…

Elon Musk is wrong about the dangers of machine learning and artificial intelligence
Despite Elon Musk's warnings this summer, there's not a whole lot of reason to lose any sleep worrying about Skynet and the Terminator. Artificial Intelligence (AI) is far from becoming a maleficent, all-knowing force. The only "Apocalypse"…

Breached Deloitte Talks About the Cost of Cyber Breaches and Hacks
Long after intruders are removed and public scrutiny has faded, the impacts from a cyberattack can reverberate over a multi-year timeline. Legal costs can cascade as stolen data is leveraged in various ways over time; it can take years to recover…

A nice civilized EDC pocket knife: Benchmade Bugout Axis
My Benchmade Bugout Axis knife arrived last week. I’ve been using it as an everyday carry (EDC) knife, instead of my usual Benchmade Griptilian or Mini Griptilian.
Summary: The Bugout is very nice and light, with an excellent blade.…

The root cause of the Equifax breach: Sheer human incompetence
Stupidity. Incompetence. Negligence. The unprecedented huge data breach at Equifax has dominated the news cycle, infuriating IT managers, security experts, legislators, and attorneys — and scaring consumers. It appears that sensitive personally…

The amazing HP calculators of the 1970s
At the current rate of rainfall, when will your local reservoir overflow its banks? If you shoot a rocket at an angle of 60 degrees into a headwind, how far will it fly with 40 pounds of propellant and a 5-pound payload? Assuming a 100-month…
Many on-prem ERP and CRM packages are not sufficiently secured
When was the last time most organizations discussed the security of their Oracle E-Business Suite? How about SAP S/4HANA? Microsoft Dynamics? IBM’s DB2? Discussions about on-prem server software security too often begin and end with ensuring…
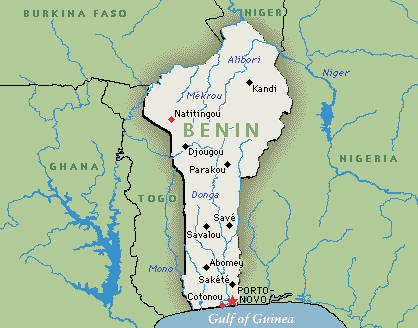
U.S. Secretary of State Rex Tillerson is spamming me from Benin
To think, the U.S. Secretary of State wants to send me money! Interesting that he’s using a gmail.com address for outgoing mail, a German email address for replies, and a phone number in the African country of Benin.
Obviously, this is…
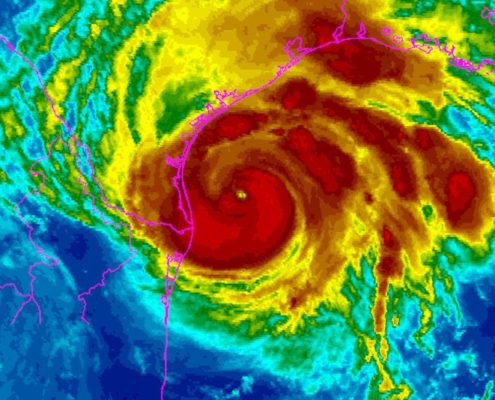
When natural disasters strike, the cloud can aid recovery
The water is rising up over your desktops, your servers, and your data center. Glug, glug, gurgle.
You’d better hope that the disaster recovery plans included the word “offsite.” Hope the backup IT site wasn’t another local business…

Cyberwar: Can Navy ships like the USS John S. McCain be hacked?
The more advanced the military technology, the greater the opportunities for intentional or unintentional failure in a cyberwar. As Scotty says in Star Trek III: The Search for Spock, “The more they overthink the plumbing, the easier it is…

The GDPR says you must reveal personal data breaches
No organization likes to reveal that its network has been breached, or it data has been stolen by hackers or disclosed through human error. Yet under the European Union’s new General Data Protection Regulation (GDPR), breaches must be disclosed.
The…

Get ready for huge fines if you don’t comply with the GDPR
The European Union is taking computer security, data breaches, and individual privacy seriously. The EU’s General Data Protection Regulation (GDPR) will take effect on May 25, 2018 – but it’s not only a regulation for companies based…

Attack of the Killer Social Media Robots!
The late, great science fiction writer Isaac Asimov frequently referred to the “Frankenstein Complex,” That was deep-seated and irrational phobia that robots (i.e, artificial intelligence) would rise up and destroy their creators. Whether…

A very cute infographic: 10 Marketing lessons from Apple
It’s hard to know which was better: The pitch for my writing about an infographic, or the infographic itself.
About the pitch: The writer said, “I've been tasked with the job of raising some awareness around the graphic (in the hope that…

Cybersecurity pros are hard to get —here’s how to find and keep them
It’s difficult to recruit qualified security staff because there are more openings than humans to fill them. It’s also difficult to retain IT security professionals because someone else is always hiring. But don't worry: Unless you work…

Ransomware dominates the Black Hat 2017 conference
“Ransomware! Ransomware! Ransomware!” Those words may lack the timeless resonance of Steve Ballmer’s epic “Developers! Developers! Developers!” scream in 2000, but ransomware was seemingly an obsession or at Black Hat USA 2017, happening…

Things in Valerian that reminded me of Star Wars and other movies
We saw “Valerian and the City of a Thousand Planets” and thoroughly enjoyed it. It was far better than the professional reviews; yes, the plot was a bit convoluted, and the yes, the romance between the major and the sergeant seemed forced…

Lloyds of London tallies the billion-dollar cost of extreme cyberattacks
A major global cyberattack could cost US$53 billion of economic losses. That’s on the scale of a catastrophic disaster like 2012’s Hurricane Sandy.
Lloyds of London, the famous insurance company, partnered with Cyence, a risk analysis…
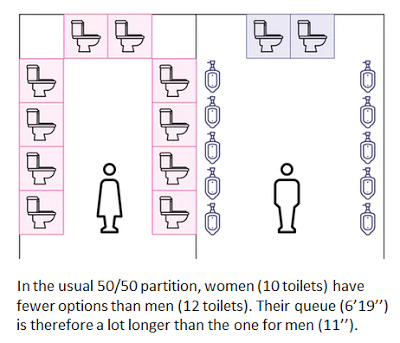
Women wait longer for a toilet — here’s how to fix it
People Queue Magazine has a fascinating new article, “No more queuing at the ladies’ room.” You’ll want to read the whole thing, because it has some fascinating mathematics (this is a scientific article, not a sociological one). Here’s…

Learn datacenter principles from ISO 26262 standards for automotive safety engineering
In my everyday life, I trust that if I make a panic stop, my car's antilock brake system will work. The hardware, software, and servos will work together to ensure that my wheels don't lock up—helping me avoid an accident. If that's not…

Oooh, my photo/face and personality will be in a scammer’s movie!
Isn't this exciting? Here's an email received that promises me a significant payout ($620,000) for, well, am not really sure. I'm sure the scam would require paying some up-front fee and/or handing over bank account information. If you receive…

Say hello to Phoenix’s Gilded Flicker
We added a new friend to our back yard bird list, the Gilded Flicker, a type of woodpecker. We already knew about our Gila Woodpeckers, and also the more common Northern Flicker, but the Gilded Flicker really stood out. See those beautiful yellow/gold…

No more mansplaining: 10 commandments for male clergy – and all lay leaders
"Thou shalt not refer winkingly to my taking off my robe after worship as disrobing." A powerful new essay by Pastor Melissa Florer-Bixler, “10 commandments for male clergy,” highlights the challenges that female clergy endure in a patriarchal…
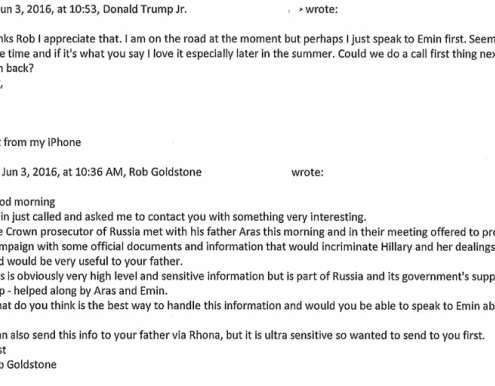
Email exchanges about Russian involvement with Don Trump Jr. are despicable
This is what Daffy Duck would describe as “dethpicable.” Absolutely deplorable.
We can now read emails exchanged last year between Don Trump Jr. (the president's son) and Rob Goldstein, an intermediary with Russia. According to Mr.…

Two degrees of separation from General Erich Ludendorff
General Erich Ludendorff, one of the top German generals during World War I, was a prominent character in the recent “Wonder Woman” movie. In the movie, General Ludendorff was killed by Diana Prince. In reality, the general survived the…
