Z Trek: The Alan Zeichick Weblog

Cybersecurity alert: Trusted websites can harbor malware, thanks to savvy hackers
According to a recent study, 46% of the top one million websites are considered risky. Why? Because the homepage or background ad sites are running software with known vulnerabilities, the site was categorized as a known bad for phishing or…

Edgescan loves to do what most people hate. Lucky you!
“If you give your security team the work they hate to do day in and day out, you won’t be able to retain that team.” Eoin Keary should know. As founder, director and CTO of edgescan, a fast-growing managed security service provider…
Why does the FTC spammer have an email address at my domain?
This is a good one. The spam message was short and sweet:
From: Richard Kent email hidden; JavaScript is required
Subj: You've been subpoenaed by the FTC.
You've been subpoenaed by the FTC.
FTC Subpoena
Please get back to me about this.
Thank…

Hello, Hibiscus! One of our favorite flowers
This plant in our garden keeps blooming and blooming. What's funny is that sometimes the flowers are yellow, and sometimes they are orange, like this one.

No honor: You can’t trust cybercriminals any more
Once upon a time, goes the story, there was honor between thieves and victims. They held a member of your family for ransom; you paid the ransom; they left you alone. The local mob boss demanded protection money; if you didn’t pay, your business…

Goodbye, Pebble – It’s a real loss to smart watches
I was dismayed this morning to find an email from Pebble — the smart watch folks — essentially announcing their demise. The company is no longer a viable concern, says the message, and the assets of the company are being sold to Fitbit.…

Four ways enterprise IT can reduce mobile risk
From company-issued tablets to BYOD (bring your own device) smartphones, employees are making the case that mobile devices are essential for productivity, job satisfaction, and competitive advantage. Except in the most regulated industries,…

Blindspotter: Big Data and machine learning can help detect early-stage hack attacks
When an employee account is compromised by malware, the malware establishes a foothold on the user’s computer – and immediately tries to gain access to additional resources. It turns out that with the right data gathering tools, and with…

Where’s the best Java coding style guide? Not at Oracle
For programmers, a language style guide is essential for helping learn a language’s standards. A style guide also can resolve potential ambiguities in syntax and usage. Interestingly, though, the official Code Conventions for the Java Programming…

Bald eagle at Canyon Lake, Arizona
What an amazing sight! We visited Canyon Lake, Arizona — a short drive from our home in Phoenix — and were rewarded with a close-up of this bald eagle. The bird seems to have caught prey; we believe it was a smaller bird, since we could…

Medical devices – the wild west for cybersecurity vulnerabilities and savvy hackers
Medical devices are incredibly vulnerable to hacking attacks. In some cases it’s because of software defects that allow for exploits, like buffer overflows, SQL injection or insecure direct object references. In other cases, you can blame…
We need a new browser security default: Privacy mode for external, untrusted or email links
Be paranoid! When you visit a website for the first time, it can learn a lot about you. If you have cookies on your computer from one of the site’s partners, it can see what else you have been doing. And it can place cookies onto your computer…

Hackathons are great for learning — and great for the industry too
Are you a coder? Architect? Database guru? Network engineer? Mobile developer? User-experience expert? If you have hands-on tech skills, get those hands dirty at a Hackathon.
Full disclosure: Years ago, I thought Hackathons were, well, silly.…

May you be blessed
Today's beautiful cactus flowers will be gone tomorrow.
So much of our world’s wonders are ephemeral. Blink and you’ll miss the rainbow. A hug lasts mere seconds. A smile is fleeting. Shapes in the clouds constantly change.
Take a…

Spammers really want to give me a BMW, but aren’t sure of the year or model
Mrs. Rachael Adams is back, and still wants to give me a fine Bavarian automobile. But is it a 7-series or a 5-series? Is it a 2015 or 2016 model? Doesn’t matter – it’s a scam. Just like the one a few weeks ago, also from Mrs. Adams,…
Though this Medium: using of Internet has been greatly Abused, says scammer
Spam scam: Who needs stand-up comedians when laughs appears in my inbox each and every day? This is one of the most amusing in a while, mainly because I can’t parse most of it.
Don’t reply to messages like this. Delete them right away.
From:…
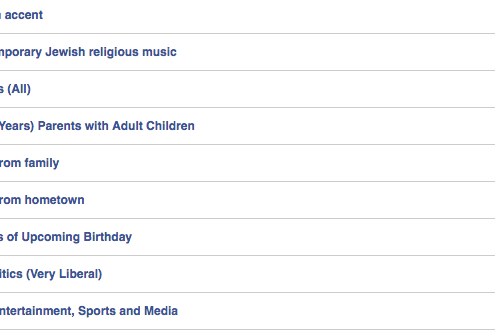
With Big Data, Facebook knows you by the company you keep
As Aesop wrote in his short fable, “The Donkey and His Purchaser,” you can quite accurately judge people by the company they keep.
I am “very liberal,” believes Facebook. If you know me, you are probably not surprised by that. However,…

When meeting to exchange goods bought online, be safe and careful
Nothing is scarier than getting together with a buyer (or a seller) to exchange dollars for a product advertised on Craig’s List, eBay or another online service… and then be mugged or robbed. There are certainly plenty of news stories on…

Securely disposing of computers with spinning or solid state drives
Can someone steal the data off your old computer? The short answer is yes. A determined criminal can grab the bits, including documents, images, spreadsheets, and even passwords.
If you donate, sell or recycle a computer, whoever gets hold…

Keep your business secrets safe with web filtering
Web filtering. The phrase connotes keeping employees from spending too much time monitoring Beanie Baby auctions on eBay, and stopping school children from encountering (accidentally or deliberately) naughty images on the internet. Were it that…
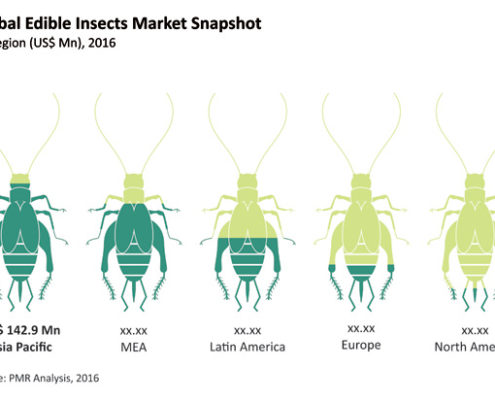
Beetle Bars and Cricket Cookies: The Global Market for Edible Insects
As a technology analyst, I read a lot of market reports. Most are not as crunchy (and unpalatable) as the Global Market Study on Edible Insects, by Persistence Market Research.
Some takeaways from the report’s summary:
In terms of value,…

People or programs: What’s the best for your synagogue?
This essay was originally published on the Reform Judaism blog on July 27, 2016.
What is the most important part of your house of worship? Is it the spiritual well-being of the community or good attendance at adult classes and innovative…

IOC Approves Amateur Radio for Tokyo 2020 Olympic Games
CQ CQ CQ de IOC: The Organising Committee for the Tokyo 2020 Games have approved new competitions to celebrate Amateur Radio.
Tokyo 2020 President Yoshiro Mori said, “The inclusion of Amateur Radio will afford athletes the chance of a lifetime…

Oracle’s reputation as community steward of Java EE is mixed
What’s it going to mean for Java? When Oracle purchased Sun Microsystems that was one of the biggest questions on the minds of many software developers, and indeed, the entire industry. In an April 2009 blog post, “Oracle, Sun, Winners,…

Pick up… or click on… the latest issue of Java Magazine
The newest issue of the second-best software development publication is out – and it’s a doozy. You’ll definitely want to read the July/August 2016 issue of Java Magazine.
(The #1 publication in this space is my own Software Development…

5 things you should know about email unsubscribe links
Here's a popular article that I wrote on email security for Sophos' "Naked Security" blog.
"5 things you should know about email unsubscribe links before you click" starts with:
We all get emails we don’t want, and cleaning them up…
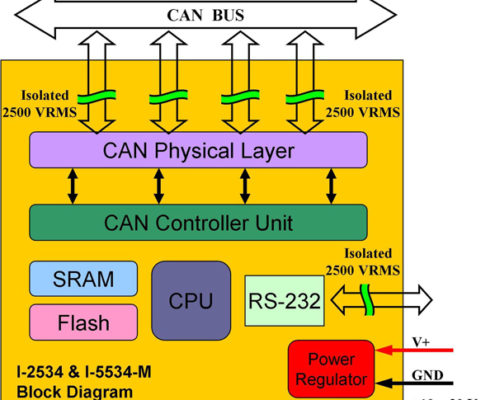
Driving risks out of embedded automotive software
When it comes to cars, safety means more than strong brakes, good tires, a safety cage, and lots of airbags. It also means software that won't betray you; software that doesn't pose a risk to life and property; software that's working for you,…

Popular news websites can be malware delivery systems
News websites are an irresistible target for hackers because they are so popular. Why? because they are trusted brands, and because — by their very nature — they contain many external links and use lots of outside content providers and analytics/tracking…

A free BMW 7-Series car – and a check for $1.5 million!
Look what I fished out of my spam folder this morning. This is a variation on the usual lottery scam, and more enjoyable than most. But really, a BMW 760Li? While the 6.6-litre twin-turbo Rolls Royce engine would be zippy on Phoenix-area highways,…

Quick-draw: Six-shooter or smartphone?
The modern gunslinger carries an iPhone on his belt, across from the six-shooter. If the phone rings, hope he doesn’t grab the wrong device.
Prescott, Arizona, July 24, 2016.
