Z Trek: The Alan Zeichick Weblog
Blast from the past: Facebook’s tech infrastructure from 2008
Fire up the WABAC Machine, Mr. Peabody: In June 2008, I wrote a piece for MIT Technology Review explaining “How Facebook Works.”
The story started with this:
Facebook is a wonderful example of the network effect, in which the value…

The glacial pace of cellular security standards: From 3GPP to 5G
Security standards for cellular communications are pretty much invisible. The security standards, created by groups like the 3GPP, play out behind the scenes, embedded into broader cellular protocols like 3G, 4G, LTE and the oft-discussed forthcoming…

Paying a steep price in Bitcoins for security lapses, thanks to ransomware
Ransomware is a huge problem that causes real harm to businesses and individuals. Technology service providers are gearing up to fight these cyberattacks – and that’s coming none too soon.
Ransomware is a type of cyberattack where bad…

States of confusion: Arizona, Colorado, New Mexico and Utah
It's bad enough not knowing which state you are in. Much worse not to know which state!
(Road trip, July 2014)

Open source is eating carrier OSS and BSS stacks, and that’s a good thing
Forget vendor lock-in: Carrier operation support systems (OSS) and business support systems (BSS) are going open source. And so are many of the other parts of the software stack that drive the end-to-end services within and between carrier networks.
That’s…

Apple WWDC 2016 becomes Apple WTF – No show stoppers there
San Francisco – Apple’s Worldwide Developer Conference 2016 had plenty of developers. Plenty of WWDC news about updated operating systems, redesigned apps, sexy APIs, expansion of Apple Pay and a long-awaited version of Siri for the Macintosh.
Call…

FAA Administrator Michael Huerta takes the main stage at InterDrone 2016
You’ve gotta be there! Michael Huerta was just announced as Grand Opening Keynote at InterDrone, the industry’s most important drone conference.
BZ Media’s InterDrone will be Sept 7-9, 2016, in Las Vegas. (I am the “Z” of BZ…

A Seven-Point Plan for Automotive Cybersecurity
I am hoovering directly from the blog of my friend Arthur Hicken, the Code Curmudgeon:
Last week with Alan Zeichick and I did a webinar for Parasoft on automotive cybersecurity. Now Alan thinks that cybersecurity is an odd term, especially…

What you can do about ransomware
Have you done your backups lately? If not… now is the time, thanks to ransomware. Ransomware is a huge problem that’s causing real harm to businesses and individuals. Technology service providers are gearing up to fight these cyberattacks…

Dell’s EMC Deal is a Good Move for Customers, Industry
Get used to new names. Instead of Dell the computer company, think Dell Technologies. Instead of EMC, think Dell EMC. So far, it seems that VMware won’t be renamed Dell VMware, but one never can tell. (They've come a long way since PC's…
A Man, a Plan, a Canal – Panama Papers and Shadow IT
The Panama Papers should be a wake-up call to every CEO, COO, CTO and CIO in every company.
Yes, it’s good that alleged malfeasance by governments and big institutions came to light. However, it’s also clear that many companies simply…

The most important plug-in for Customer Experience Management software: Humans
No smart software would make the angry customer less angry. No customer relationship management platform could understand the problem. No sophisticated HubSpot or Salesforce or Marketo algorithm could be able to comprehend that a piece of artwork,…

Too slow, didn’t wait: The five modern causes of slow website loads
Let's explore the causes of slow website loads. There are obviously some delays that are beyond our control — like the user being on a very slow mobile connection. However, for the most part, our website’s load time is entirely up to us.
For…

Sauron hacks the Internet of Rings as a state sponsor of cyberterrorism
Barcelona, Mobile World Congress 2016—IoT success isn’t about device features, like long-life batteries, factory-floor sensors and snazzy designer wristbands. The real power, the real value, of the Internet of Things is in the data being…

Wearable IoT technology is getting under my skin, thanks to bodyhacking
CeBIT Preview, Hannover, Germany — It looks like a slick Jedi move, but it's actually the Internet of Things. When Hannes Sjöblad wants to pay for coffee, he waves his hand in front of the pay station. When he wants to open a door, he…

Hackathons build community
A hackathon – like the debut LSO Hackathon held in November 2015 at the MEF’s GEN15 conference – is where magic happens. It's where theory turns into practice, and the state of the art advances. Dozens of techies sitting in a room, hunched…
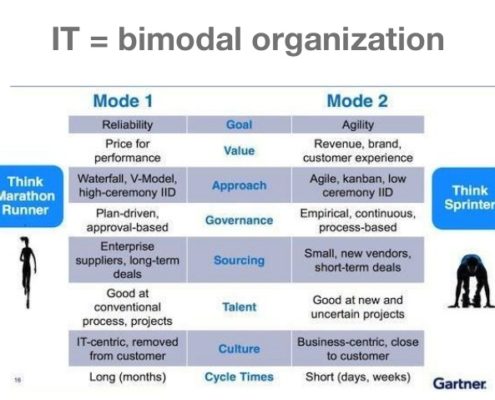
Bimodal IT — safety and accuracy vs. speed and agility
Las Vegas, December 2015 — Get ready for Bimodal IT. That’s the message from the Gartner Application, Architecture, Development & Integration Summit (AADI). It wasn’t a subtle message. Bimodal was a veritable drumbeat, pounded home…

Before I die, I want to know the Face of God
This essay was originally published on the Reform Judaism blog on September 2, 2015.
I was inspired to write this poem after reading Rabbi Eliezer’s teaching in Pirkei Avot that advises us that because it is not possible to repent one day…

How to handle difficult feedback without losing your cool
Your app’s user interface is terrible. Your business plan is flawed. Your budget is a pipe dream. Your code isn’t efficient. Clients are unhappy with your interpersonal skills. Your meetings are too long. You don’t seem to get along with…

Succession planning is an integral piece of your leadership portfolio
This essay was first published on the Reform Judaism blog on July 6, 2015.
In the Torah portion Pinchas, God instructs Moses,
“Ascend these heights of Abarim and view the land that I have given to the Israelite people. When you have…

Finding authentic Reform Judaism
This essay was first published on the Reform Judaism blog, and was adapted from an article I wrote in December 2013 for the monthly Bulletin of Peninsula Temple Sholom in Burlingame, Calif.
Some Jewish families light Shabbat candles every…

Big Security, Big Cloud and the Big Goodbye
Software-defined networks and Network Functions Virtualization will redefine enterprise computing and change the dynamics of the cloud. Data thefts and professional hacks will grow, and development teams will shift their focus from adding new…

Innovate in the cloud, cheaply and securely
For development teams, cloud computing is enthralling. Where’s the best place for distributed developers, telecommuters and contractors to reach the code repository? In the cloud. Where do you want the high-performance build servers? At a…

Attack of the six-rotor quadracopter photo drones
Drones are everywhere. Literally. My friend Steve, a wedding photographer, always includes drone shots. Drones are used by the military, of course, as well as spy agencies. They are used by public service agencies, like fire departments. By…

Is the best place for data in your data center or in the cloud? Ask your lawyer
Cloud-based storage is amazing. Simply amazing. That’s especially true when you are talking about data from end users that are accessing your applications via the public Internet.
If you store data in your local data center, you have…

Once upon a midnight dreary, while I struggled with jQuery
SEYTON
The tests, my lord, have failed.
MACBETH
I should have used a promise;
There would have been an object ready made.
Tomorrow, and tomorrow, and tomorrow,
Loops o’er this petty code in endless mire,
To the last iteration of recorded…

The wisdom, innovation, and net neutrality of Bob Metcalfe
Washington, D.C. — “It’s not time to regulate and control and tax the Internet.” Those are words of wisdom about Net Neutrality from Dr. Robert Metcalfe, inventor of Ethernet, held here at the MEF GEN14, the annual conference from the…

Under Satya Nadella, Microsoft is getting stuff done
I like this new Microsoft. Satya Nadella’s Microsoft. Yes, the CEO needs to improve his public speaking skills, at least when talking to women’s conferences. Yet when you look at the company’s recent activities, what appears are lots of…
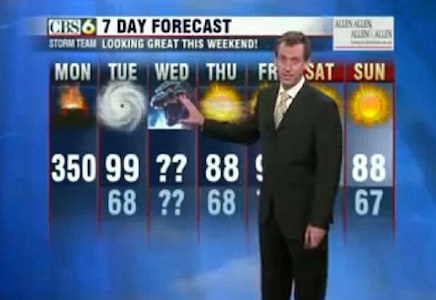
Tomorrow’s forecast: Distributed Denial of Service
Malicious agents can crash a website by implementing a DDoS—a Distributed Denial of Service Attack—against a server. So can sloppy programmers.
Take, for example, the National Weather Service’s website, operated by the United States…
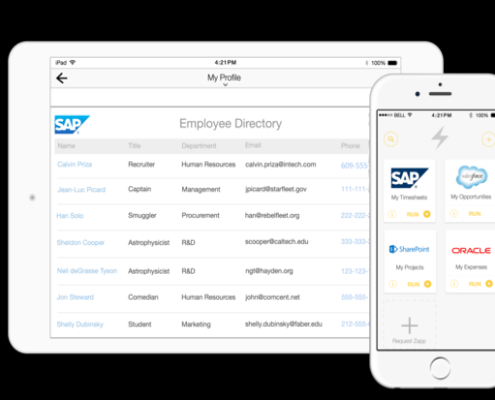
Capriza’s clever mobility via HTML screen scraping
HTML browser virtualization, not APIs, may be the best way to mobilize existing enterprise applications like SAP ERP, Oracle E-Business Suite or Microsoft Dynamics.
At least, that’s the perspective of Capriza, a company offering a SaaS-based…
