The subject line in today’s email from United Airlines was friendly. “Alan, it’s been a while since your last trip from Austin.”
Friendly, yes. Effective? Not at all close.
Alan, you see, lives in northern California, not in central Texas. Alan rarely goes to Austin. Alan has never originated a round trip from Austin.
My most recent trip to Austin was from SFO to AUS on Feb. 13, 2011, returning on Feb. 15, 2011. The trip before that? In 2007.
Technically United is correct. It indeed has been a while since my last trip from Austin. Who cares? Why in the world would United News & Deals — the “from” name on that marketing email— think that I would be looking for discounted round-trip flights from Austin?
It is Big Data gone bad.
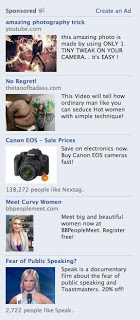
We see example of this all the time. A friend loves to post snarky screen shots of totally off-base Facebook ads, like the one that offered him ways to “meet big and beautiful women now,” or non-stop ads for luxury vehicles. For some reason, Lexus finds his demographic irresistible. However: My friend and his wife live in Manhattan. They don’t own or want a car.
Behavioral ad targeting relies upon Big Data techniques. Clearly, those techniques are not always effective, as the dating, car-sales and air travel messages demonstrate. There is both art and science to Big Data – gathering the vast quantities of data, processing it quickly and intelligently, and of course, using the information effectively to drive a business purpose like behavioral marketing.
Sometimes it works. Oops, sometimes it doesn’t. Being accurate isn’t the same as being useful.
Where to learn that art and science? Let me suggest Big Data TechCon. Three days, dozens of practical how-to classes that will teach you and your team how to get Big Data right. No, it’s not in Austin— it’s near Boston, from April 8-10, 2013. Hope to see you there— especially if you work for United Airlines or Lexus.











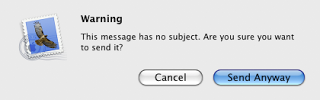 Among the most peevish of my pet peeves are email messages that have no subject line. Why do people send them?
Among the most peevish of my pet peeves are email messages that have no subject line. Why do people send them?






 A decade ago, Ms. Garnett made a whole bunch of lonely programmers’ days. Is that really the type of trail-blazing attention that a woman tech-industry entrepreneur believes she must seek out? Today, is Avatar Partners so desperate for publicity that their public relations agency must tout the physical attributes of the company’s female CEO? Pathetic.
A decade ago, Ms. Garnett made a whole bunch of lonely programmers’ days. Is that really the type of trail-blazing attention that a woman tech-industry entrepreneur believes she must seek out? Today, is Avatar Partners so desperate for publicity that their public relations agency must tout the physical attributes of the company’s female CEO? Pathetic.
 Welcome to my blog. It has to start somewhere, and this is where it starts. And the trek had to start sometime; it should have started a long time ago, but it didn’t, so here we are.
Welcome to my blog. It has to start somewhere, and this is where it starts. And the trek had to start sometime; it should have started a long time ago, but it didn’t, so here we are.